4.2: The Classical Persuasion Model
- Page ID
- 3934
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)According to Lasswell (1948), all communication should be analyzed in terms of who (Source) says what (Message), via what medium (Channel), to whom (Receiver), and directed at what kind of change (Effect). This classical persuasion model, which is depicted in Figure 4-1, was further articulated by Hovland, Janis and Kelley (1953) and has remained the predominant conceptual approach in the field of communication, and especially research on persuasive communication (McGuire, 1969, 1985; O’Keefe, 1990).
Research guided by this model has found sources are perceived primarily in terms of expertise and trustworthiness, but also by other characteristics such as status, likeability, and attractiveness. Similar to French and Raven’s (1959; Raven, 1964) definitions of expert and information power, a source’s expertise is defined by its information about a situation and knowledge about cause-and-effect relationships in the environment. By contrast, trustworthiness refers to a source’s willingness and ability to provide accurate information and take actions that protect the receiver without seeking hidden advantage for him- or herself.
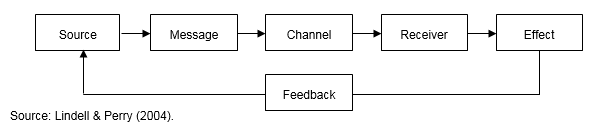
Figure 4-1. The Classical Persuasion Model.
Messages vary in their content—especially their information about a hazard, its impact characteristics (e.g., magnitude, location, and time of impact), potential personal consequences (e.g., likelihood of casualties, property damage, and social disruption), alternative protective actions (e.g., evacuation, sheltering in-place), and the attributes of those protective actions (e.g., efficacy; safety; cost; and requirements for time and effort, knowledge and skill, tools and equipment, and cooperation from others). In addition, messages also vary in terms of their style (clarity, forcefulness, and speed of delivery, use of figurative or humorous language), inclusions and omissions (whether or not to include one’s own weak arguments, address opponents’ arguments, or to rely on implicit or explicit conclusions), ordering of message content, and amount of message material (McGuire, 1985).
The information channels available for use by emergency managers include print media such as newspapers, magazines, and brochures; electronic media such as television, radio, telephone, and the Internet; and face-to-face interaction through personal conversations and public meetings. The distinctions among these information channels are important because they differ in the ways they accommodate the information processing activities of receivers. For example, orally presented information is ephemeral and will be lost unless otherwise recorded, whereas written information inherently provides a record that can be examined at a later time. Moreover, many types of risk information can be presented in either verbal (words), numeric (numbers), or graphic (pictures) format. Sometimes one mode of presentation is more effective for a particular type of information; for example, charts generally are more effective than tables of numbers in conveying trends. However, there are individual differences among receivers, so some presentation modes are more effective for some people but not others. For example, some people can understand verbal descriptions much more readily than graphs of data, whereas the reverse is true for others.
Receivers differ in many respects, but the most important of these are psychological characteristics that have direct effects on the communication process. For example, receivers differ in their perceptions of source credibility, access to communication channels, prior beliefs about hazards and protective actions, ability to understand and remember message content, and access to resources needed to implement protective action (Lindell & Perry, 2004). The effects of a message on a receiver include attention, comprehension, acceptance, retention, and behavioral change. Indeed, researchers agree message effects should be characterized in terms of multiple stages, but the boundaries among these stages are not well defined, so differences exist among various researchers in their typologies (see McGuire, 1985 vs. Mileti & Peek, 2001) and some theorists have varied in their definitions of these stages over time (McGuire, 1969, 1985).
Finally, feedback is an important component of the communication model because some attempts are unidirectional, whereas others are interactive. Unidirectional communications are appealing to many risk communicators because they appear to be less time consuming and sometimes this actually is the case. Frequently, however, interactive communication is needed for receivers to indicate they have not comprehended the message that was sent or to explain that the message sent by the source did not satisfy their information needs.
The classical persuasion model makes it clear that risk communication is an activity with relatively clearly defined parameters regarding source, message, channel, and intended effect. In most cases, the source is an authority, the message describes an environmental hazard, and the intended effect is a change in receivers’ behavior. However, receiver characteristics have very important influences on each of the stages in the communication process. For example, the effect of a given information source is determined by receivers’ perceptions of that source and the effect of a given message is determined by receivers’ willingness to attend to and ability to comprehend and retain the information. Moreover the effect of a given channel is determined by receivers’ access to and preference for that channel and the amount of feedback depends upon receivers’ willingness and ability to provide it. Unfortunately, authorities often fail to recognize the importance of these factors and sometimes fail to design risk communication programs in accordance with the principles of effective communication even when these issues are recognized (Perry & Lindell, 1991).
Some scholars have criticized the classical persuasion model as providing an incomplete representation of the risk communication process (Kasperson & Stallen, 1990). They contend the feedback loop in the model implies a dyadic relationship that is limited to contact with the original information source. However, extensive research shows people engage in information seeking activities that are directed to other sources as well. More generally, risk communication should be represented by a network in which multiple sources are linked to intermediate sources who receive information and relay it to the ultimate receivers (Figure 4-2). The original sources could be linked to few or many intermediates or could even be linked directly with some of the ultimate receivers. Similarly, the intermediates could be linked to few or many of the ultimate receivers and the ultimate receivers could be linked to each other.
Another apparent limitation of the classical persuasion model is that receiver characteristics have pervasive effects on the other components of the model. For example, receivers’ demographic characteristics are correlated with access to sources and channels, as well as with message comprehension. Thus, receiver characteristics are of critical importance in determining the success of risk communication programs, but many of them are psychological in nature and, thus, not readily observed. Nonetheless, receivers’ demographic characteristics—such as sex, age, education, income, race, and ethnicity—are readily identifiable. Because some of these demographic characteristics are related to relevant psychological characteristics, they can provide some indication as to how receivers will respond.

