8.1: Safeguarding Computers and Networks
- Page ID
- 32024
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)- Identify risks and associated mitigation strategies for addressing computer virus.
- Identify risks and associated mitigation strategies for data loss and backup.

Understanding and Addressing Cybersecurity Threats in Schools
Educational technology includes all the digital tools and resources used for teaching and learning, like computers, tablets, software, and online platforms. These technologies help improve the learning experience and prepare students for a world driven by technology. However, as schools rely more on technology, they become more vulnerable to cybersecurity threats. Schools need to protect student and staff information and academic records from unauthorized access. Threats like hacking, phishing scams, and malware pose serious risks. It is important for schools to put in place strong security measures. Understanding these threats is the first step toward creating a safe learning environment that uses technology to enrich education while reducing risks. In this chapter, we explain common security issues and suggest strategies to enhance safety.
Schools depend on technology for teaching and learning. But this reliance also creates challenges, especially with computer and network security. Those working in education need to understand basic digital security to ensure a safe learning environment. The goal is to safeguard sensitive information and provide smooth technology access without disruptions from security breaches.
Image generated using DALL·E 3 (CC BY)
Computer Viruses and Security
You've probably heard the term "computer virus." Like biological viruses, computer viruses are programs designed to spread from one computer to another and infect systems. This can lead to data loss and corruption. There are other harmful programs too, like ransomware, spyware, and worms. Each works differently to cause problems. For example, ransomware can lock important teaching materials until a payment is made to release them.
Schools need to take proactive steps to combat threats. The information technology (IT) department usually leads security efforts. But it’s important for everyone to understand and follow their recommendations. Some strategies include:
- Using antivirus software to detect and stop threats before they cause damage. This acts as a shield.
- Being careful about opening email attachments and links from unknown senders. These often spread viruses.
- Regularly updating software. Updates fix vulnerabilities so malware can’t get in as easily.
Ensuring Safety and Continuity in School Networks

Think of network security as your school’s digital fortress. Firewalls and secure Wi-Fi work like walls and a moat, keeping out invaders. Physical security measures also help. These include locking server rooms and tethering equipment in place. This stops people from accessing your school’s digital assets without permission.
The IT department usually handles network security. But it’s good for all users to understand the basics. That way you can help keep the networks safe. Small steps like using strong passwords and not clicking risky links go a long way.
Image generated using DALL·E 3 (CC BY)
Importance of Vigilant Security Practices
It’s extremely important to protect student records, grades, and other school data. If this information gets out, it could lead to identity theft or cheating. Schools need clear rules on who can access what information. Training staff and students also helps. Phishing simulations teach people to spot and report real phishing emails. This boosts the human side of cybersecurity.
Comprehensive Backup and Recovery Approaches

It’s not just about keeping intruders out. Schools also need plans to avoid losing important data and materials. For example, what if a teacher loses all their lesson plans due to a computer crash? Without backups, weeks of work could vanish.
Regular backups help prevent these disasters. Cloud backup services automatically store file copies securely offline. If files go missing, the school can restore the backups. Schools usually have policies for saving and managing data.
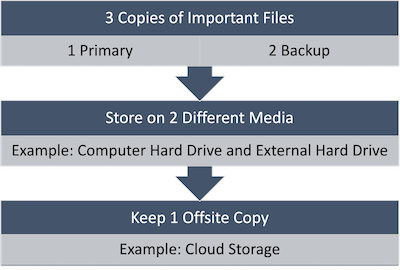 Image generated using DALL·E 3 (CC BY)
Image generated using DALL·E 3 (CC BY)
Data Recovery and Backup Strategy Implementation
Developing a backup and recovery strategy is crucial. This involves not only regularly scheduled backups but also regular drills to restore data from backups, ensuring that the process is foolproof. Schools should employ strategies that follow the 3-2-1 backup rule: keep three copies of any important file (one primary and two backups), store the files on two different media types, and keep one copy offsite (Krogh, 2009). Keeping school technology secure takes layers of defense against threats. It also means having plans to get back on track when problems happen. The key is making security part of everyday routines. Teachers and staff should build awareness around current cyber risks for schools.
Figure 8.1.1 3-2-1 Backup Rule (Krough, 2009) by Renee Albrecht (CC BY).
Krogh, P. (2009). The Dam Book: Digital Asset Management for photographers. O’Reilly.


