5.3: Networking Concepts and Processes
- Page ID
- 5653
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Ethernet is the dominant type of network installed in schools; it uses cables (consisting of eight strands of copper wires and shielding to prevent electromagnetic fields from interfering with the signal) that connect to ports in computers, switches, and other devices with plastic clips that close circuits throughout the network. Regardless of the size of the network, data rate, addressing, and Efficacious Educational Technology 98 routing are characteristics that determine how its robustness and reliability.
Data Rate or Bandwidth
Data rate refers to the amount of information that can be transferred over a network in a given time; the term bandwidth is also used to describe data rate. Ever since networks were installed in schools, IT managers have sought to provide broadband access to schools, this term refers to connections to circuits providing the greatest available data rate.
Broadband the term used to describe “large amounts of bandwidth,” but it is a relative term. In 2015, the Federal Communication Commission in the United States of America increased the minimum data rate for connections to be considered broadband to 25 megabits per second (Mbps). In a commonly-cited summary of Internet speeds, Akamai (2017) reported the average connection speed in the United States was 18.7 Mbps. While that is several times faster than the global average (7.2 Mbps), it is much slower than those countries with the fastest average broadband connections. These measurements of data rate are difficult to place in a meaningful context, but the simple observation “the more bandwidth the better the performance of the network” is correct. IT professionals in school enter into contracts with a local Internet service provider (perhaps a telephone company, perhaps a cable television provider) to access a connection to the Internet with a specified bandwidth. The bandwidth provided by the ISP depends on the nature of their circuits and the price the school budgets to pay for the service.
The bandwidth available to users in at a location is limited by the bandwidth of the connection to outside circuits, and bandwidth is a zero-sum quantity. A system administrator might complain, “when those students start streaming music, they are using up all of our bandwidth.” The students are using the finite capacity of the network to transfer information to listen to music, thus it is unavailable for other uses.
All network devices (including the network adapters installed in computers) have a data rating, which reflects that maximum amount of information that can pass through device per unit of time. The first Ethernet networks installed in schools typically used 10Base-T devices which had a maximum data rate of 10 Mbps (megabits per second). It is difficult to understand exactly what that means, but it is important to know those devices were replaced with 100Base-T devices around the turn of the century, and those have largely been replaced with devices rated at 1 Gbps (gigabits per second), and many IT professionals have “future proofed” their networks by upgrading LAN devices to data ratings of 10 Gbps. These new network devices can move data 1000 times more data in a given time than the networks first installed in schools. While an IT manager who has installed 10 Gbps devices can rest assured that the network is likely to be robust and reliable, they know they will replace these devices with devices with greater capacity in the coming years.
The total data rate of a network connection is determined by the device in the network that has the least data rate. Consider a school in which all of the devices were upgraded to provide 1 Gbps data rate, except for the switch that serves the computersin one wing of the school where a 100 Mbps switch remained. In that wing, the greatest possible data rate would be 100 Mbps. Further, if one of the teachers in that wing is using an older computer in which the network interface card (which connects a computer to the network) was rated at 10 Mbps, then that teacher’s maximum data rate would be limited by that card. For users in the wing connected through the 100 Mbps switch, an especially that teacher connecting through a 10 Mbps network interface card, the more reliable and robust 1 Gbps network would not be enjoyed.
Factors other than the data rate rating of devices contribute to the actual performance of the devices as well. Many network devices (such as switches) include a small computer and software that helps with sending packets of information to the correct address and other functions. Just like all computers, if those are asked to perform too many functions, they stop working; those frozen processors can reduce data rate to almost zero. The effects of an overloaded gateway can be particularly troublesome as all network traffic flows through it to the Internet. I was once asked to help troubleshoot a network with curious symptoms. Early in the day and late in the day, the network performed adequately for the few adults who were in the building and using the network. Once students arrived and began sending and receiving traffic over the network, it slowed to a crawl and the data rate was about 1% of what was provided by the ISP. The technology coordinator was convinced the problem was due to increased traffic due to computer that was infected with malware, but there was no evidence of a specific computer generating excessive traffic when the symptoms were demonstrated and LAN traffic was unaffected. As it turned out, the network had been configured so that a single switch was responsible for managing much of the network traffic; the result was the switch was unable to handle the traffic and, despite it being rated a 1 Gbps, its effective data rate was a small fraction of maximum. Once network management was shared among several devices, performance returned to normal.
If the maximum bandwidth available from the local ISP is inadequate for the demands of a schools, then the IT professionals must purchase additional lines and divide the network traffic between them; this arrangement provides more robust and reliable availability during those times when network demand is greatest as there is extra bandwidth to handle to extra demands. In recent years, many schools have converted to voice over Internet protocol (VOIP) telephone services. Because of the importance for robust and reliable telephone service to schools, IT professionals will work with the vendors who provide the system to ensure it is served by adequate bandwidth (most often with a connection to the Internet that is separate from the data network). Changes such as these typically require expertise beyond that of the LAN administrator employed by the school, so they hire network engineers to ensure the reconfigured network provides necessary operation during the switch over.
The data rate needed by an organization is heavily affected by the nature of the data being transferred. A text document contains relatively little information, so sending a word processing document over a network consumes little bandwidth; video, on the other hand, contains great amounts of information, thus consumes much bandwidth to transfer. The network demands of a classroom full of students reading Wikipedia pages will be far less than a classroom full of students watching YouTube videos. This explains why many technology coordinators and network administrators will limit access to “broadband hogs” like YouTube by decreasing the bandwidth available to and from the site. They can configure routing and switching to minimize the bandwidth that is available to transmit packets from those sites.
Measuring data rate or connection speed is a very easy task, and it is one of the first steps in troubleshooting a network that is not performing as expected. There are a number of web sites that can be used to perform a speed test for a connection. This is accomplished by the sending files of known size to and from your computer. Time stamps on the packets are used to determine the actual bandwidth of the connection from the user to the site.
Another step in troubleshooting unreliable, and non-robust networks is for an IT system administrator to use packet analyzing software to observe the network traffic in detail. In the vernacular, this is called “network sniffing.” Using this software provides one with many details of which nodes are using bandwidth and for which purposes. Computers found to be generating excessive or questionable traffic by analyzing the packets originating from it and passing to it can help IT administrators identify malfunctioning or malware-infected computers. Consider, for example, some Internet games transmit traffic using a specific hypertext transfer protocol port. System administrators can configure the network to not use those ports, thus preventing access to the Internet gaming site from the school network.
Addressing
Each device on a computer network must have a unique address. This is unsurprising as networks operate when information is sent from one node to another, and without a unique address, it would be impossible for packets of information to make it to the correct location. There are two types of addresses (one that never changes and one that varies each time a computer connects to a network), and understanding networking requires knowledge of each.
Every hardware device that connects to a network has a media access control (MAC) address, which is sometimes called the physical address of the device, which is programmed into the hardware when it is manufactured. This address never changes, and it is useful for identifying with precision a computer or device on a network; networks sniffers, of example, will be able to identify the MAC address for every device sending or receiving packets.
Software on a single network device (perhaps a server or router or gateway or unified threat management appliance) has dynamic host configuration protocol (DHCP) operating, and it assigns Internet protocol (IP) addresses to devices attached to the network. The IP address is a temporary address; each time a device connects to a new network it is given an IP address for that session. On its next connection to the network, the device may be assigned the same address or it may be assigned a different one. The DHCP server is configured to have a pool of addresses that can be assigned, when the pool is exhausted, no more devices can be connected.
Into the second decade of the 21st century, Internet addresses were assigned following the rules known as IPv4 (Internet protocol version four), so every Internet node was assigned a quaddot address which consists of four numbers separated by dots, for example 192.168.1.100. Each IPv4 address consisted of 32 bits, so the Internet consisted of up to 232 (almost 4.3 billion) nodes. Because that number of address was going to be exhausted (which would have stopped the growth of the Internet), computer systems have been configured to use IPv6 (Internet protocol version six), which uses 128 bits to identify an IP address. This expands the number of possible Internet nodes to 2128 (3.4 x 1038); an example of an IP address written in IVv6:
2001:0db8:85a3:0000:0000:8a2e:0370:7334
Almost every network is configured to allow information to be addressed to nodes using either version of the protocol, and IPv4 is still used to configure LAN’s.
Internet protocol addresses in either IPv4 or IPv6 are strings of digits, or digits and letters, so they are difficult for humans to remember. So that World Wide Web sites can be accessed via names that are meaningful to humans, domains name servers (DNS) are connected to networks and these convert the universal resource locator (URL) such as http://www.google.com of a web site into its IP address. Occasionally a computer will malfunction in a curious manner; it will appear as if it is connected and some network operations will continue to function, but users cannot open web sites unless one knows the IP. In this case, the technician is likely to say, “It is not resolving addresses,” and he or she will track down and resolve DNS problems on the machine.
Gateways which are the devices through which all of the computers on a school LAN connect to the Internet have at least two network adapters. The external adapter is assigned the gateway’s IP address on the Internet which is set by the ISP. All traffic requested from the Internet by a computer on the LAN will be sent to that external IP address. The traffic then passes to the circuits that comprise the LAN and the internal adapter of the gateway is set with a static IP address. Software on the gateway differentiates packets of information requested by a LAN IP from those incoming packets that originated from elsewhere and have not been requested. IT 2001:0db8:85a3:0000:0000:8a2e:0370:7334 security professionals spend much time ensuring incoming data that is not authorized is not allowed to pass into the LAN.
Each network has 255 addresses (in reality, subnets are used to increase the number of addresses, but let’s keep it simple in this example). Following the model of an IPv4 quad dot address, one can assign 192.168.0.1 through 192.168.0.255 (the first three sets of digits are always the same on a subnet). These 255 addresses comprise the pool of addresses that can are assigned and managed by the single DHCP server on the network. A system administrator uses up to three options when configuring the DHCP server; two are used on almost every school network, and the third is used less frequently.
First, devices that are always connected to the LAN and always powered on (such as switches, wireless access points, threat management appliances, and printers) are given static IP addresses. This type of IP address is configured in the network settings on the device, and then it is removed from the pool of addresses assigned by the DHCP server. Often, the LAN administrator removes a series of IP addresses from those that can be assigned dynamically, then assigns those to devices necessitating static IP addresses. Devices are assigned static IP addresses when they are likely to receive frequent connections from throughout the network, so both humans and computers benefit from increased performance by always using the same address. In effect, a static IP address establishes a permanent IP address so the IP address and MAC address are both unchanging (until the IP address is changed on the devices by an IT administrator).
Second, devices that are connected intermittently (including desktop and laptop computers, Internet-only notebooks, and mobile devices) are assigned a new address each time it connects by the DHCP server; this is called a dynamic IP address as it frequently changes. The system administrator will typically specify the IP addresses that can be assigned, and once that pool is exhausted, no mode device can connect to the network until the system administrator configures another subnet on the LAN.
A third option, which is less commonly used is to have the DHCP server assign an IP address that is reserved for the device each time it is connected to the network; of course, this method is not really dynamic, but it differs from a static IP address as it is assigned by the DHCP server, and not configured on the device itself. Reserved IP addresses are removed from the pool of dynamically assigned addresses as well. This method is most often used when configuring a static IP addresses requires unfamiliar steps. Some technical schools, for example, connect simulated electrical panels and other industrial interfaces to their networks for training purposes. The computers on the panels cannot be accessed using a familiar graphic user interface, so configuring the static IP address is done by the server rather than configured into the device.
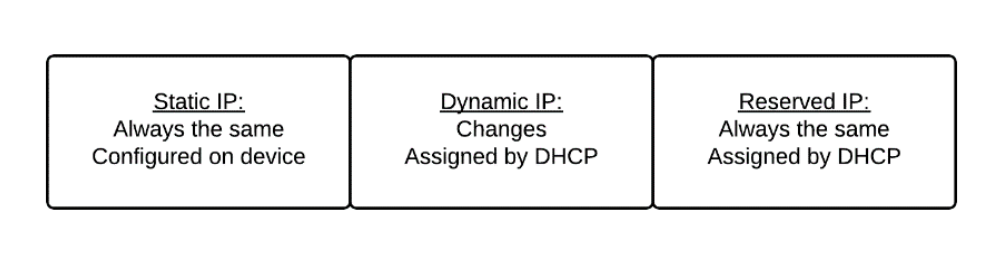
Figure \(\PageIndex{1}\): Three options for assigning IP addresses
Routing
For networks to function, packets of information must make it to the correct destination. This depends on accurate addressing and also on effective routing. As the name suggests, a routing is the network function in which packets are sent via a route to their destination. Routing occurs between the LAN and the Internet and this is accomplished through a device called a router (or more likely this function is assigned to routing software on a network appliance that serves multiple roles).
Within the LAN, information packets are routed by devices called switches. The unmanaged consumer switch that one can purchase at the office supply store for $50; it works with the default configuration (which cannot be changed) for the small number of devices it connects. The switches on enterprise networks are have sophisticated software that allows them to manage packets sent to and from many more nodes and rules for how packets are sent and received can be configured. This software is one of the reasons enterprise switches cost about ten times the cost of consumer switches per port.

