1.5: The Role of Theory
- Page ID
- 5627
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)In the vernacular, “theory” is associated with ideas that are incomplete or not necessarily true. Among educators, and other pragmatic professionals such as technologists, theory is often associated with unrealistic or idealistic thinking that has little connection to their work. Those interpretations of theory are unfortunate, however, as theory can inform and focus decisions made by all who participate in school IT management. It is reasoned that making decisions and taking actions without addressing theory leads to inefficient and ineffective decisions and actions.
Grounding decisions and actions in theory allows decision makers to take advantage of three affordances that make it particularly useful for efficacious IT management in schools. First, every theory clearly identifies those factors that are relevant and that deserve managers’ attention as they design interventions. Even when professionals are working within their field of expertise, they often overlook important factors, they dedicate resources to irrelevant factors, or they accept assumptions that have been disproven by research. Theory supports the design of interventions that focus on what matters and only what matters.
Second, theory allows IT managers to predict the changes that will be observed once decisions are implemented. Coincidentally, theory suggests methods for collecting data that will confirm or refute those predictions. Although instruments designed to collect research data may not be appropriate for evaluating interventions in schools, theory has been elucidated with instruments and methods that can be can be adapted by IT managers as they seek to evaluate management decisions and actions in schools.
Third, theory affords explanations. The reason researchers do their work is to identify and support cause-and-effect relationships. While it is exceedingly difficult to establish cause- and-effect without experimenting (and true randomized double- blind experiments are unusual in education for a range of factors including ethical considerations), theory can facilitate our understanding why IT projects in schools failed or succeeded. If our predictions are accurate, then we explain them in terms of theory. If our predictions fail, then we use theory to understand what happened and why. In both cases, theory results in deeper understanding of our unique situations and the decisions we make and actions we take.
Several theories and frameworks relevant to IT management in schools are presented in this book. Educational technology is a field in which some work can be conducted from an atheoretical stance. The technician repairing computers has little concern for theory, but teachers’ actions are informed by theory (even if it is not articulated). Theory, nevertheless, plays an important role in how managers undertake their work and in providing a structure within which technicians, teachers, and all others who contribute to the technology-rich school function. Without theory, IT managers are likely to abandon interventions before they have matured to the point where expected improvements are widely observed as they are distracted by emerging fads that promise unreasonable outcomes.
There are two theories have been widely applied to problems in educational technology and these can be used to explain and predict many situations and the results of many interventions in the field. When there appears to be no other theory to inform decisions and evidence, technology acceptance model and cognitive load theory can provide insight for IT managers.
Technology Acceptance
Technology acceptance model was first elucidated to understand the observation “that performance gains are often obstructed by users' unwillingness to accept and use available systems” (Davis, 1989 p. 319), and it has been used to study decisions to use (or avoid) technology in many settings. Variations of technology acceptance model have been used to develop and refine both IT systems (hardware and software) and organizational practices that rely on IT systems. It is used to predict and explain both how individuals interact with IT as well as patterns of IT use within groups, and it is used to change perceptions of technology and patterns of technology use.
In 2003, Venkatesh, Morris, Davis and Davis modified the TAM into the Unified Theory of Acceptance and Use of Technology (UTAUT); in this work, the scholars combined eight different theories that predict the decision to use technology into one model. According to UTAUT, four factors are positively associated with the use of technology: performance expectancy, effort expectancy, social influences, and facilitating conditions (see Figure 1.6.1).
- Performance expectancy is a measure of the extent to which an individual believes technology will affect his or her job performance in a positive manner. It is rooted in efficiency, relative advantage, and outcome expectations. Interventions that lead to increased efficiency or improved outcomes will be more used.
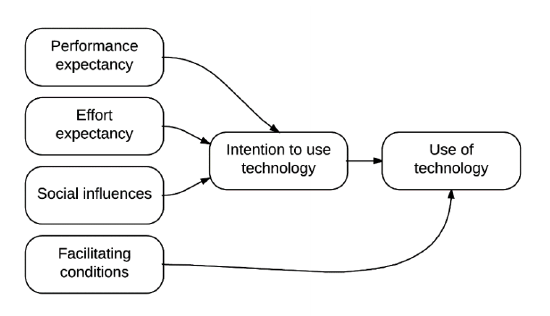
Figure \(\PageIndex{1}\): Factors directly associated with technology use (adapted from Venkatesh, Morris, Davis and Davis 2003)
- Effort expectancy is a measure of the individual’s perceptions of how easy it is to use the technology; users intend to use systems they perceive to be easy-to-use.
- Social influences are related to the individual’s perceptions of how others perceive the technology and its use; technology used by others who opinion is valued will be more used.
- Facilitating conditions include structures that provide responsive and effective technical support, adequate replacement plans, access to necessary training, and other supports. More and more highly functioning systems that maintain and provide technology in organizations are associated with increased use of it.
It is notable that these factors are associated with ones’ intention to use a technology are based on each individual’s perceptions. In a school, different populations and even different individuals within a population may perceive the same technology differently, and those differences will affect individuals’ intentions to use the technology. Efficacious IT managers will use UTAUT as a theory to explain observed uses of technology and predict interventions that will change those patterns. Changes can be made to affect those factors, and failures to observe the expected changes can be evaluated for either effectiveness or perceptions of the changes.
Cognitive Load Theory
While technology acceptance is a theory that can explain and predict the decision to use a technology, cognitive load theory (Sweller, Ayres, & Kalyuga, 2011) (CLT) predicts and explains technology use once it has been adopted. CLT is based on the assumption that using information (and the information technologies used to communicate it) requires attention, perception, thought, and memory, thus it is a cognitive activity. Further, human cognition is a zero-sum quantity; each individual has a limited quantity of cognition available at any moment, and that cognition used for one purpose is not available for another purpose.
Theorists identify three types of cognitive load that characterize an information task:
- Intrinsic cognitive load is that which is necessary to understand the task and to use the information necessary to accomplish the task. Changing the task changes the intrinsic cognitive load, and steps taken to reduce it results in a different task.
- Germane cognitive load is that which is available for the learner to think about, strategize about, and come to deeper understanding of the ideas and information in the task. Learning occurs only when germane cognitive load is available and the amount available limits what can be learned.
- Extraneous cognitive load is that which is wasted by the learners managing bad design or poor organization of information or information technology tools. Using unfamiliar tools can also increase extraneous cognitive load.
When designing the information tasks and the information technology platforms that are used for teaching and learning, efficacious IT managers seek to minimize extraneous cognitive load and maximize germane cognitive load. It is reasoned that changing the intrinsic cognitive load is accomplished only by changing the task; therefore, reducing the extraneous cognitive load is the only method of increasing the cognitive load for germane purposes.
Consider the example of graphing calculators. Using this technology, one can minimize the extraneous cognitive load of drawing the graph of a sophisticated function, so more cognition can be dedicated to understanding the mathematics. When first encountering a graphing calculator (or when encountering an unfamiliar model), determining how to use the device increases extraneous cognitive load of graphing. This explains the practice of introducing such technology with simple and familiar examples. Once the technology and its operation along with the manner in which it displays information becomes familiar, the extraneous cognitive load of using it decreases, so the advantage of using it for sophisticated mathematics is realized.
As with all theory, CLT predicts and explains what may be observed in technology-mediated teaching. Devices may be unused and procedures may be avoided because they introduce excessive extraneous cognitive load. It also helps IT managers understand the changing perceptions of and uses of technologies; as technology solutions become more familiar (through training and familiarity) they should become more widely used.

