5.1.5: Basics of Databases Wrap-Up
- Page ID
- 10125
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Let’s Summarize
In this unit we have been looking at databases—their purpose, structure, uses, and applications in the business arena, particularly in the area of customer service. First, a database is a computer-based collection of related pieces of data organized so that the data can readily be accessed, managed, and updated. Database software is the phrase used to describe any software that is designed for creating databases and managing the information stored in them. There are relational and non-relational databases. Sometimes referred to as database management systems (DBMS), database software tools are primarily used for storing, modifying, extracting, and searching for information within a database. Database software is used for a number of reasons in any industry - from keeping your bookkeeping on task, compiling client lists to running your online eCommerce site. Examples include Oracle Database, MySQL, Microsoft SQL Server, and IBM DB2. Some of these programs support non-relational databases, but they are primarily used for relational database management. Examples of non-relational databases include Apache HBase, IBM Domino, and Oracle NoSQL Database.
Basic Organization of a Database
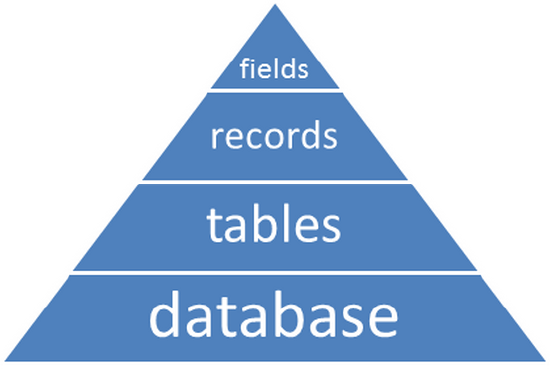
A database is composed of tables (and the queries, reports and other forms that are generated from data in the tables). The tables are composed of records, and the records contain fields.
Interacting with a Database
Database software or program, also called a database management system (DBMS) allows users to interact with the database at all levels of the hierarchy. Some of the interactions are characterized as
- data entry form— a window on the screen that allows the user to enter data into the fields that make up a record.Data can also be modified via the form.
- a query— a way of retrieving data from the database via specification of criteria that identify exactly what data is to be retrieved and how it might be sorted and displayed. Data can also be modified via the query.
- reports— a means of retrieving selected data from the database, which the user can specify.
- file maintenance— the procedures that keep data current in the database.File maintenance supports adding, modifying, and deleting records, and creating backup copies of the database.
- wizard—a Microsoft Access software application that is used to create tables, queries, and reports.
Different Database Models
All databases are composed of the elements identified above. But the organization of the records and tables can be quite different. We briefly looked at several models.
Hierarchical and network models were the first designed but are now considered less effective and efficient because the designs are less flexible, not allowing for easy changes to the structure of the database. In the relational model, all the information about a person, place, event, etc., is stored in related records, but the information is spread across different tables. The different types of data that are used to describe an individual, place, thing, or event are linked by a common key field, called the primary key. In the object-oriented database model, the data itself is conceived of as objects. The object can consist of data (character, numeric, etc.), or it can be instructions on what to do with that data. The objects are joined by the use of pointers. The final database model is the multidimensional databasemodel, built and used optimally for data warehouse and online analytical processing applications.
Integrity and Validity of the Data
Data integritymeans that the data is verified as correct, up to date or timely, organized in a way that is useful, and accessible to the user when it is needed. Data validityis satisfied by comparing data being entered to a set of rules to ensure that the entry complies with those rules (Shelly & Vermaat, 2013).
Customer Relationship Management (CRM)
Customer relationship management is a strategy used by companies to better manage customer relationships. CRM is defined very broadly because it includes many facets of business-to-customer relationships. But the following might be considered the primary focus of any CRM system:
- acquisition—obtaining new customers
- retention—retaining current customers
- loyalty—developing customer loyalty to the company and/or product
- profitability—increasing company profits by serving the customer
- service—addressing customer inquiries and resolving issues
Relationship Among CRM, Data Warehouses, and Data Mining
Data mining is the process of looking at the data stored in a company's database to determine if statistically relevant trends exist. By identifying these trends and patterns, companies can develop strategies to better serve their customers and at the same time increase their sales. One example of data mining is the evaluation of data purchased from a company that specializes in collecting demographic datato determine which individuals might have a need for the company’s product or services.
How It Works
Almost all CRM applications involve using a large relational database, sometimes referred to as a data warehouse, where raw data about customers, products, transactions, demographics, and other information is stored. Using complex statistical analysis software programs known as data mining tools, data analysts are able to query the data warehouse in a multitude of ways.
There are real business benefits associated with improving customer relationships and offering great customer service. Research shows that companies that make customer experience a priority generate higher profits than their competitors. Because it is more cost effective to retain current customers than to attract new ones, establishing and maintaining a good relationship with customers is critical to the financial bottom line.
Social Relationship Management (SCRM)
Customers and potential customers are coming to businesses through more and different pathways than ever before, using mobile devices and social media sites instead of relying only on the telephone. As a result, many companies are turning to CRM systems that include social media integration. This new CRM is typically called social CRM, or SCRM. To keep pace with changing customer expectations, CRMs must be sensitive to the following issues and tasks in making sure the CRM system is effective and efficient.
- Increased customer expectations. Customers demand the capability to interact with a company beyond the traditional phone call.
- Keeping valuable staff. Proper CRM training, support, and state-of-the-art tools to recruit and retain CRM staff should be the focus. An agent needs to know how to handle the various means by which customers interact with the company personnel, and how to use the consumer's information appropriately to solve problems.
- Privacy.Companies need to foster a strong sense of trust in the relationship if they expect to continue to have customers share data freely.
- Mining the social media inputs. Social media analytics, the gathering of data from blogs and social media websites for analysis in order to make business decisions, is gaining importance in businesses. This process helps marketers, sales personnel, and contact center agents observe customers' social output and respond accordingly to any talk about their brand.
- Cleaning up the data. Incorrect and duplicative data can add wasted time and efforts to the work of call center or sales employees. It also can lead to errors and missed opportunities.
Databases and Security Issues
It is the confidentiality, integrity, and availability (CIA) of the data in a database that need to be protected. Confidentiality can be lost if an unauthorized person gains entry or access to a database, or if a person who is authorized to view selected records in a database accesses other records he or she should not be able to view. If the data is altered by someone who is unauthorized to do so, the result is a loss of data integrity. And if those who need to have access to the database and its services are blocked from doing so, there is a resulting loss of availability.
Security of any database is significantly impacted by any one or more of these basic components of CIA being violated. The following is a summary of the most common causes of database breaches.
Threats
- unauthorized access by insiders
- incorrect usage
- unprotected personal hardware collection
- stolen laptops
- weak authentication
- exploiting weaknesses in an operating system or network
- theft of database backup tapes or hard drives
Vulnerabilities
- data at rest (unencrypted information) that is passively residing in storage
- data in motion, in the course of being electronically transmitted outside the company’s protected network
- poor architecture, in which security was not adequately factored into the design and development of the database
- vendor bugs, particularly programming flaws that allow actions to take place within the database and with the data that were not intended or planned
- an unlocked database, in which no access restrictions or auditing security measures are in place
Risk Assessments
In the business environment, it is critical that a thorough risk assessment take place and be periodically reviewed. The assessment should address who has access to and control of the database, database security software, and training.
How Can You Protect Your PII?
Protecting databases and the data contained within can be a costly and all-consuming activity. Obviously, you cannot implement security measures for the company, business, or government agency that holds your PII. But there are measures you can take to better protect yourself:
- Keep passwords to yourself.
- Use different passwords for different accounts.
- Use strong passwords.
- Check your credit reports annually.
- Control physical access to your devices.
- Remember to log out or lock your computer when you are finished using it.
- Remember to lock your computer with a password when you are finished using it.
Quiz
Before you do the quiz activity, please evaluate your understanding of the learning objectives for the Basics of Databases module and use the first My Response link below to ask any questions you might have about the material that you would like the instructor to address. Your questions can be for clarification of the material or further insight. Your self-evaluation will not be graded, but will be available for your instructor to read. Answering these questions may also shape the discussions in class.
About Basics of Databases
If you do not feel ready for the quiz, identify the objectives you need to review. Go back to those pages. Read the examples and do the activities. Don’t just read the activities, actually do them to get practice with the types of questions that will be in the quiz.
Basics of Databases Module
Now that you have finished the quiz, do you have any questions? Your instructor will be able to read the questions and comments that you submit.
References
- Shelly, G. B., & Vermaat, M. E. (2013). Discovering Computers 2013. Boston: Course Technology.

