7.3: Reading- Security and Social Issues
- Page ID
- 18660
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Security Within the Organization

Security risks within an organization include the processing of fraudulent transactions, unauthorized access to data and program files, and the physical theft or damage of equipment.
Fraud
Computer fraud is increasing at an alarming rate. Fraud can be defined as the manipulation of the records of an organization to conceal an illegal act (normally the theft of funds or other assets). Computers can make it easy for employees in particular to defraud the organization, in particular when the level of security and internal control is lax. In manual systems, a common control to limit fraud is to involve two or more people in a process, each one effectively controlling the activities of the others. We call this control process separation of duties. For example in a payroll system one might give an individual the authority to approve increases, another the task of updating the computer and the third the responsibility to distribute funds to employees. Without collusion between them, it would be difficult for any one of these individuals to steal funds from the payroll system and hide his tracks. Unfortunately, in many computer systems, too many separate functions have been computerized and often there is a single clerk responsible for running the entire payroll process. In these situations, anyone who has access to the application can take the opportunity to commit fraud. The most common fraud tactics are:
- Entering fictitious transactions. Most frauds are committed by employees using the system in the normal way to enter fictitious transactions. No special technical knowledge is required and the employee relies on the fact that management supervision of the process in weak.
- Modification of computer files. Normally requires a little more technical expertise as this would involve, for example, the increase or reduction of amounts held on the master file, which cannot be changed within the application without an appropriate transaction (such as a payment).
- Unauthorized changes to programs. This type of fraud is usually limited to staff with programming expertise. A common example is the skimming or salami technique. In a payroll system this would entail deducting a small amount from each individual salary cheque and adding the total to a select individual’s payment. The secret behind this technique is that employees are unlikely to notice a change in their salary (PAYE and other deductions often cause regular variation in the total) and the total payroll will balance (the total amount being paid is the same.)
How does an organization limit fraud? Experts suggest a three-pronged attack. Firstly the organization must stress the need for honesty and ethical behavior in all business activities. Managers must lead by example, new employees must be screened and staff training must support this theme. The second concern is the level of opportunity in the organization to commit fraud. There must be strong internal controls, separation of duties, restricted access to sensitive applications and constant management supervision. Audit trails are used to record the origin of every transaction, and sequential numbering ensures that records cannot be deleted or reports destroyed. Finally, where a case of fraud is discovered, action must be taken against the offender. Many organizations prefer not to prosecute employees suspected of fraudulent behavior because of the negative publicity they will receive in the press. This in itself encourages criminals to repeat the activity in their new working environment knowing the likelihood of punishment is remote.
Unauthorized Data Access
Password protection is the most common method of protecting corporate data. Nevertheless, fraudulent transactions are often carried out by unauthorized users who manage to gain access to the corporate network by using the login details of another user. One way of achieving this is through a terminal spoof – a simple yet effective approach to finding other user’s passwords. A terminal spoof is a program that runs on a machine and looks like the normal login screen. Once a user has given his or her user-id and password, the terminal spoof will record both on the local disk or server, give what looks like an authentic error message (such as invalid password – please re-enter) and then passes control to the real login program. The criminal will pick up the passwords later to gain access to the system masquerading as the unfortunate victim.
Other criminals simply make use of an unattended computer that has been left on by a user who has logged in to the network and then left the office. Time-out or screen-saver programs with password protection provide a simple barrier to this approach In addition, locked doors are a traditional means of excluding undesirable visitors.
Other dangers of which managers should be aware include the Trojan horse, in which code is added to a program, which will activate under certain conditions. For example, a computer consultant in Johannesburg had a client in Durban. He placed a Trojan horse in the payroll program so that it would malfunction while processing the June payroll. They would fly him down, all expenses paid, to fix the problem and stay for the Durban July horse race. Once this had happened for the third time, another consultant was used who uncovered the offending code.
Another risk is the Back-door technique. When programmers are building systems, they may try to bypass all the access security procedures to speed up the development time. In some cases, these “back doors” have not been removed and the programmer can gain illegal entry into the production system.
Sabotage and Theft
When computers were the size of small houses and hidden in secure computer installations, then theft of computer hardware was rare. Today, PCs are on most desks and in many cases they have to be physically bolted to the table to prevent their disappearance. One famous case of theft involved a laptop computer stolen from the back seat of a car in the USA in early 1991. On the hard disk was the master plan for Desert Storm, the details of how the United States and her allies would attack Iraq.
Mobile computing devices are especially vulnerable to theft, and limiting of physical access to equipment is the most effective first line of defense. Restrictions to entry can be based on electronic locks, activated by means of magnetic disks or swipe cards, or on advanced biometric devices that identify the individual based on characteristics such as fingerprints or the pattern of the retina. (In each case, the security mechanism would obviously be linked to a database containing details of authorized users.)
Another form of theft relates to the copying of programs and data resources in an organization. Obtaining customer lists together with the details of the amount and type of business can obviously assist companies to encourage customers away from their competition. Theft of software is a major problem in the PC world where users often make illegal copies of the programs rather than purchase the package themselves – this practice is known as software piracy. This type of theft is more difficult to identify, since the original product has not physically disappeared as with the theft of computer hardware. Where software piracy is discovered, the owner of the computer on which the software resides (often the employer) is held to be legally responsible for the presence of pirated software.
The last category of computer theft covers the illegal use of computer time. In the past computer operators were often caught processing work for third parties or users were doing their own work at the office. Computer hackers spend their time searching for networks to which they can gain access. Having breached the security controls, they often browse around the databases in the installation but may not do any damage. In these instances, the only crime they can be charged with is the theft of computer time.
Security Beyond the Organization
Hackers and Firewalls

Hackers are users from outside the organization, who penetrate a computer system usually through its communication lines. Although some hackers are content merely to demonstrate that they have bypassed network security, there is a high risk of malicious damage to data, stealing of sensitive information (such as customers’ credit card numbers) or entry of fraudulent transactions by the hacker. Hackers may also instigate a denial-of-service attack, in which a targeted web site is inundated with requests for information initiated by the hacker, rendering it inaccessible for genuine business customers.
A firewall is an additional system that enforces access control policy between two networks, especially between a corporate network and the Internet. The firewall monitors all external communications, checks user authorization and maintains a log of all attempts to access the network. They can also be used to check for the presence of viruses, for the downloading of unauthorized software, and to guard against denial-of-service attacks.
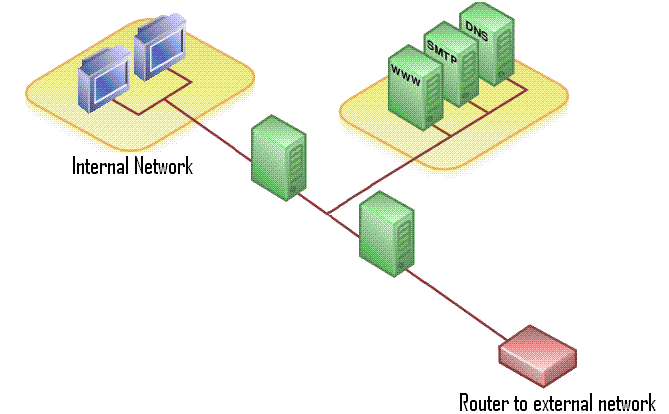
Data which is in the process of being communicated is also vulnerable to eavesdropping. Encryption, which scrambles data into an unreadable form, can be used to improve data privacy and prevent any unauthorized changes to the message, as well as protecting the confidentiality of data within the organization.
Viruses
A computer virus is a program that invades a computer system, normally by residing in corrupt files. The virus has the ability to replicate itself and so spread to other files and computer systems. Some viruses are benign and merely advertise their presence, but others corrupt the files they infect and even destroy entire databases.
There are three main types of viruses. The original viruses were mainly systems viruses. They resided in the boot sector of a disk (the first place the computer looks when loading the operating system) or in the operating system utilities. These viruses were usually easy to find and clean. One problem was that they loaded into memory as soon as an infected machine was switched on and could often hide themselves from the anti-viral software.
The next generation of viruses attached themselves to executable files. When an infected program is run, the virus resides in memory and infects all new programs run until the system is switched off. These viruses are difficult to counter, especially on a network as common files are often infected. Even when the file server is cleared of infected programs, users have copies on their personal hard drives, or a infected copy of the program in memory when the virus check is performed on the server.
One area most users with which felt safe was the accessing of non-executable files such as word processing documents. Unfortunately there are now a number of macro viruses that can attach themselves to documents and spreadsheets. Even receiving a simple letter as an e-mail attachment can infect your machine. Some of the more well known viruses include:
- Michelangelo. This virus infected many machines in the early months of 1992. The virus was primed to activate on Michelango’s birthday (6th March) and had the capability of destroying all files on the hard disk of infected PC’s. News of the virus made headlines and many businessmen and home users rushed out to purchase programs to check and clean viruses from their installations. On the day, some infections did occur but the main winners were the vendors of virus detection software.
- Stoned. A very common virus in the late 1980s it came in many forms, some harmless while others corrupted files by attacking the directories and allocation tables. The main theme of the virus was to legalize the smoking of cannabis and normally the message “Your PC is now Stoned” would appear on the screen.
- Jerusalem. Deletes all programs that are run on Friday 13th.
- Concept. A macro virus, attached to word processing documents.
- EXEBUG. A nasty little bug that may corrupt your hard drive. This is a systems virus and can infect the CMOS of your PC. Very difficult to find and eradicate as it uses “stealth” technology to hide from virus checkers.
With increasing globalization and interorganizational communications, viruses are able to spread faster and further than ever before. Recent examples include Melissa, ILoveYou, and the Nimda virus, which make use of multiple methods of transmission. The real mystery about viruses is why they exist at all. Some experts suggest that computer hackers are motivated by the challenge of “beating the system” by writing programs that can bypass virus protection systems and take control of each individual machine. A more likely motive is to induce computer users to purchase legal copies of software. The only real winners in the new world of computer viruses are the companies selling computer software.
In the early 1980’s the illegal copying of PC software, or software piracy was rife as there was no real business advantage to purchasing the software (except a copy of the official reference manual). Today it is estimated that about 50% of the PC software used in the USA has been illegally copied and the situation in South Africa is likely to be worse. One of the major motivations for buying software rather than copying from a friend is that the shrink-wrapped product is guaranteed to be virus free.
The best line of defense against viruses is the regular use of up-to-date anti-virus software, which will scan files for viruses and remove them if found.
- Discovering Information Systems Sections 10.1-10.3. Authored by: Jean-Paul Van Belle, Mike Eccles, and Jane Nash. Located at: https://archive.org/details/ost-computer-science-discoveringinformationsystems. License: CC BY-NC-ND: Attribution-NonCommercial-NoDerivatives
- DMZ Network Diagram Two Firewalls. Authored by: Jasonlfunk. Located at: https://en.wikipedia.org/wiki/File:DMZ_network_diagram_2_firewalls.png. License: CC0: No Rights Reserved
- Vulnerable. Authored by: Jannis Blume. Located at: https://www.flickr.com/photos/iblume/6230865185/. License: CC BY-SA: Attribution-ShareAlike
- I, the Hacker. Authored by: Charis Tsevis. Located at: https://www.flickr.com/photos/tsevis/93150384/. License: CC BY-NC-ND: Attribution-NonCommercial-NoDerivatives

