6.2: The Information Security Triad- Confidentiality, Integrity, Availability (CIA)
- Page ID
- 9781
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)The Information Security Triad: Confidentiality, Integrity, Availability (CIA)
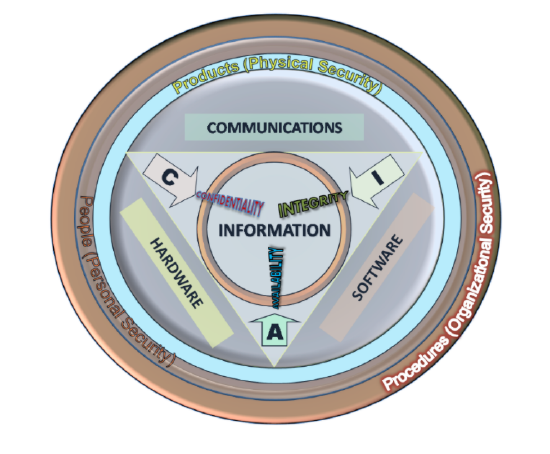
Confidentiality
Protecting information means you want to restrict access to those who are allowed to see it. This is sometimes referred to as NTK, Need to Know, and everyone else should be disallowed from learning anything about its contents. This is the essence of confidentiality. For example, federal law requires that universities restrict access to private student information. Access to grade records should be limited to those who have authorized access.
Integrity
Integrity is the assurance that the information being accessed has not been altered and truly represents what is intended. Just as people with integrity mean what they say and can be trusted to represent the truth consistently, information integrity means information truly represents its intended meaning. Information can lose its integrity through malicious intent, such as when someone who is not authorized makes a change to misrepresent something intentionally. An example of this would be when a hacker is hired to go into the university’s system and change a student’s grade.
Integrity can also be lost unintentionally, such as when a computer power surge corrupts a file or someone authorized to make a change accidentally deletes a file or enters incorrect information.
Availability
Information availability is the third part of the CIA triad. Availability means information can be accessed and modified by anyone authorized to do so in an appropriate time frame. Depending on the type of information, an appropriate timeframe can mean different things. For example, a stock trader needs information to be available immediately, while a salesperson may be happy to get sales numbers for the day in a report the next morning. Online retailers require their servers to be available twenty-four hours a day, seven days a week. Other companies may not suffer if their web servers are down for a few minutes once in a while.
You'll learn about who, what, and why of cyber-attacks in this chapter. Different people commit cybercrime for different purposes. Security Operations Centers are designed to fight cybercrime. Jobs in a Security Operations Center (SOC) can be obtained by earning certifications, seeking formal education, and using employment services to gain internship experience and job opportunities.
The Danger
In chapter 5, we discussed various security threats and possible solutions. Here are a few scenarios to illustrate how hackers trick users.
Hijacked People
Melanie stopped at her favorite coffee shop to grab her drink for the afternoon. She placed her order, paid the clerk, and waited to fulfill orders' backup while the baristas worked furiously. Melanie took her phone out, opened the wireless client, and linked to what she thought was the free wireless network for the coffee shop.
Sitting in the corner of the store, however, a hacker had just set up a free, wireless hotspot "rogue" posing as the wireless network of the coffee shop. The hacker hijacked her session when Melanie logged on to her bank's website and accessed her bank accounts.
Hijacked Companies
Jeremy, an employee of a large, publicly-held corporation's finance department, receives an email from his CEO with an enclosed file in Adobe’s PDF format. The PDF regards earnings for the organization in the third quarter. Jeremy does not recall his department making the PDF. His interest is triggered, and he opens his attachment.
The same scenario plays out around the company as thousands of other workers are enticed to click on the attachment successfully. As the PDF opens, ransomware is mounted on the workers' computers, including Jeremy’s, and the process of storing and encrypting corporate data begins. The attackers' target is financial gain, as they keep the company's ransom data until they get paid. The consequences for opening an attachment in a spam mail or from an unfamiliar address could be disastrous, as with Jeremy’s case.
Targeted Nations
Some of today's malware is so sophisticated and expensive to create that security experts believe that it could be created only by a nation-state or group of nations. This malware can be designed to attack vulnerable infrastructures, such as the water network or electric grid.
This was the aim of the Stuxnet worm, infecting USB drives. The movie World War 3.0 Zero Days tells a story of a malicious computer worm called Stuxnet. Stuxnet has been developed to penetrate Programmable Logic Controllers (PLCs) from vendors-supported nuclear installations. The worm was transmitted into the PLCs from infected USB drives and ultimately damaged centrifuges at these nuclear installations.
Threat Actors
Threat actors include amateurs, hacktivists, organized crime groups, state-funded groups, and terrorist organizations. Threat actors are individuals or a group of individuals conducting cyber-attacks on another person or organization. Cyberattacks are intentional, malicious acts intended to harm another individual or organization. The major motivations behind cyberattacks are money, politics, competition, and hatred.
Known as script kiddies, amateurs have little or no skill. They often use existing tools or instructions to start attacks found on the Internet. Some are only curious, while others seek to show off their abilities by causing damage. While they use simple methods, the outcomes can often be catastrophic.
Hacktivists
A hacktivist can act independently or as a member of an organized group. Hacktivists are hackers who rage against many social and political ideas. Hacktivists openly demonstrate against organizations or governments by publishing articles and images, leaking classified information, and crippling web infrastructure through distributed denial of service ( DDoS) attacks with illegal traffic. A denial of service (DoS) attack is one of the most powerful cyberattacks in which the attacker bombards the target with traffic requests that overwhelm the target server in an attempt to crash it. A distributed denial of service (DDoS) attack is a more sophisticated version of DoS in which a set of distributed computer systems attacks the target.
Financial Gain
The financial gain motivates much of the hacking activity that constantly threatens our security. Cyber Criminals are people who utilize technology for their own malicious intentions, such as stealing personal information to make a profit. Such cybercriminals want access to our bank accounts, personal data, and everything else they can use for cash flow generation.
Trade Secrets and Global Politics
In the past few years, several reports have been seen of nation-states hacking other nations or otherwise intervening with internal policies. National states are also keen to use cyberspace for industrial spying. Intellectual property theft can give a country a considerable advantage in international trade.
Defending against the consequences of state-sponsored cyberespionage and cyber warfare will continue to be a priority for cybersecurity professionals.
How Secure is the Internet of Things
The Internet of Things ( IoT) is rapidly expanding all around us. The internet of things is a network of physical objects that collect and share data over the internet. We're now beginning to enjoy the IoT rewards. There is a constant creation of new ways of using connected things. The IoT helps people link items so they can enhance their quality of life. Smart security systems, smart kitchen appliances, smartwatches, and smart heating systems are few examples of the IoT products available today.
For starters, many people now use connected wearable devices to monitor their fitness activities. How many devices do you currently own that link to the Internet or your home network?
How safe are those devices? For instance, who wrote the software to support the embedded hardware (aka firmware)? Has the programmer been paying attention to the security flaws? Are your home thermostats connected to the internet? Your Electronic Video Recorder (DVR)? When there are security bugs, can the firmware be patched in the system to fix the vulnerability? The new firmware will not update many computers on the Internet. For updating with patches, some older devices were not even developed. These two conditions put the users of such devices to face threats and security risks.
Reference
World War 3 Zero Days (Official Movie Site) - Own It on DVD or Digital HD. Retrieved September 6, 2020, from www.zerodaysfilm.com


