5: Networking and Communication
- Page ID
- 4400
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Learning Objectives
Upon successful completion of this chapter, you will be able to:
- understand the history and development of networking technologies;
- define the key terms associated with networking technologies;
- understand the importance of broadband technologies; and
- describe organizational networking.
Introduction
In the early days of computing, computers were seen as devices for making calculations, storing data, and automating business processes. However, as the devices evolved, it became apparent that many of the functions of telecommunications could be integrated into the computer. During the 1980s, many organizations began combining their once-separate telecommunications and information-systems departments into an information technology, or IT, department. This ability for computers to communicate with one another and, maybe more importantly, to facilitate communication between individuals and groups, has been an important factor in the growth of computing over the past several decades.
Computer networking really began in the 1960s with the birth of the Internet, as we’ll see below. However, while the Internet and web were evolving, corporate networking was also taking shape in the form of local area networks and client-server computing. In the 1990s, when the Internet came of age, Internet technologies began to pervade all areas of the organization. Now, with the Internet a global phenomenon, it would be unthinkable to have a computer that did not include communications capabilities. This chapter will review the different technologies that have been put in place to enable this communications revolution.
A Brief History of the Internet
In the Beginning: ARPANET
The story of the Internet, and networking in general, can be traced back to the late 1950s. The US was in the depths of the Cold War with the USSR, and each nation closely watched the other to determine which would gain a military or intelligence advantage. In 1957, the Soviets surprised the US with the launch of Sputnik, propelling us into the space age. In response to Sputnik, the US Government created the Advanced Research Projects Agency (ARPA), whose initial role was to ensure that the US was not surprised again. It was from ARPA, now called DARPA (Defense Advanced Research Projects Agency), that the Internet first sprang.
ARPA was the center of computing research in the 1960s, but there was just one problem: many of the computers could not talk to each other. In 1968, ARPA sent out a request for proposals for a communication technology that would allow different computers located around the country to be integrated together into one network. Twelve companies responded to the request, and a company named Bolt, Beranek, and Newman (BBN) won the contract. They began work right away and were able to complete the job just one year later: in September, 1969, the ARPANET was turned on. The first four nodes were at UCLA, Stanford, MIT, and the University of Utah.
The Internet and the World Wide Web
Over the next decade, the ARPANET grew and gained popularity. During this time, other networks also came into existence. Different organizations were connected to different networks. This led to a problem: the networks could not talk to each other. Each network used its own proprietary language, or protocol (see sidebar for the definition of protocol), to send information back and forth. This problem was solved by the invention of transmission control protocol/Internet protocol (TCP/IP). TCP/IP was designed to allow networks running on different protocols to have an intermediary protocol that would allow them to communicate. So as long as your network supported TCP/IP, you could communicate with all of the other networks running TCP/IP. TCP/IP quickly became the standard protocol and allowed networks to communicate with each other. It is from this breakthrough that we first got the term Internet, which simply means “an interconnected network of networks.”
Sidebar: An Internet Vocabulary Lesson
Networking communication is full of some very technical concepts based on some simple principles. Learn the terms below and you’ll be able to hold your own in a conversation about the Internet.
- Packet: The fundamental unit of data transmitted over the Internet. When a device intends to send a message to another device (for example, your PC sends a request to YouTube to open a video), it breaks the message down into smaller pieces, called packets. Each packet has the sender’s address, the destination address, a sequence number, and a piece of the overall message to be sent.
- Hub: A simple network device that connects other devices to the network and sends packets to all the devices connected to it.
- Bridge: A network device that connects two networks together and only allows packets through that are needed.
- Switch: A network device that connects multiple devices together and filters packets based on their destination within the connected devices.
- Router: A device that receives and analyzes packets and then routes them towards their destination. In some cases, a router will send a packet to another router; in other cases, it will send it directly to its destination.
- IP Address: Every device that communicates on the Internet, whether it be a personal computer, a tablet, a smartphone, or anything else, is assigned a unique identifying number called an IP (Internet Protocol) address. Historically, the IP-address standard used has been IPv4 (version 4), which has the format of four numbers between 0 and 255 separated by a period. For example, the domain Saylor.org has the IP address of 107.23.196.166. The IPv4 standard has a limit of 4,294,967,296 possible addresses. As the use of the Internet has proliferated, the number of IP addresses needed has grown to the point where the use of IPv4 addresses will be exhausted. This has led to the new IPv6 standard, which is currently being phased in. The IPv6 standard is formatted as eight groups of four hexadecimal digits, such as 2001:0db8:85a3:0042:1000:8a2e:0370:7334. The IPv6 standard has a limit of 3.4×1038 possible addresses. For more detail about the new IPv6 standard, see this Wikipedia article.
- Domain name: If you had to try to remember the IP address of every web server you wanted to access, the Internet would not be nearly as easy to use. A domain name is a human-friendly name for a device on the Internet. These names generally consist of a descriptive text followed by the top-level domain (TLD). For example, Wikepedia’s domain name is Wikipedia.org; Wikipedia describes the organization and .org is the top-level domain. In this case, the .org TLD is designed for nonprofit organizations. Other well-known TLDs include .com, .net, and .gov. For a complete list and description of domain names, see this Wikipedia article.
- DNS: DNS stands for “domain name system,” which acts as the directory on the Internet. When a request to access a device with a domain name is given, a DNS server is queried. It returns the IP address of the device requested, allowing for proper routing.
- Packet-switching: When a packet is sent from one device out over the Internet, it does not follow a straight path to its destination. Instead, it is passed from one router to another across the Internet until it is reaches its destination. In fact, sometimes two packets from the same message will take different routes! Sometimes, packets will arrive at their destination out of order. When this happens, the receiving device restores them to their proper order. For more details on packet-switching, see this interactive web page.
- Protocol: In computer networking, a protocol is the set of rules that allow two (or more) devices to exchange information back and forth across the network.
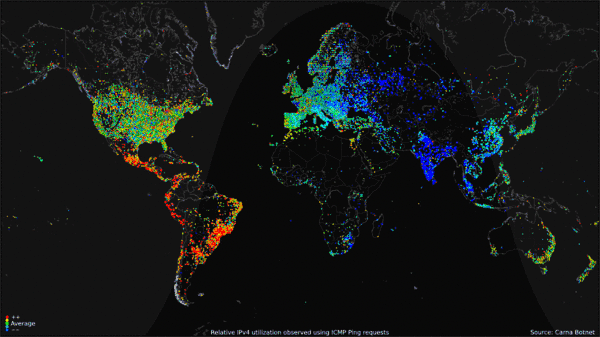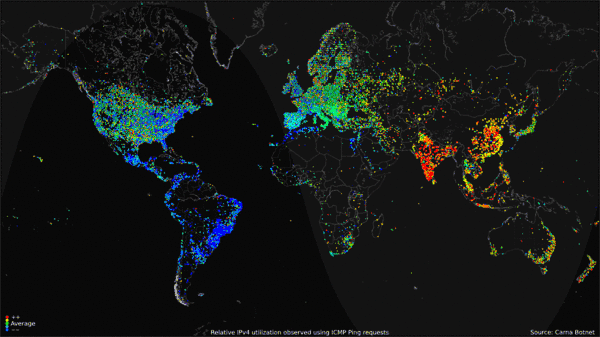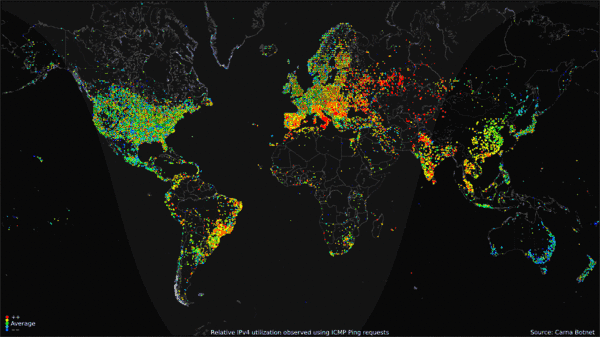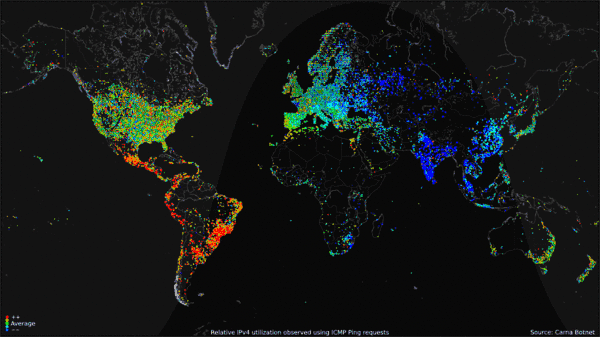
Worldwide Internet use over 24-hour period (click to go to site of origin). (Public Domain. Courtesy of the Internet Census 2012 project.)
As we moved into the 1980s, computers were added to the Internet at an increasing rate. These computers were primarily from government, academic, and research organizations. Much to the surprise of the engineers, the early popularity of the Internet was driven by the use of electronic mail (see sidebar below).
Using the Internet in these early days was not easy. In order to access information on another server, you had to know how to type in the commands necessary to access it, as well as know the name of that device. That all changed in 1990, when Tim Berners-Lee introduced his World Wide Web project, which provided an easy way to navigate the Internet through the use of linked text (hypertext). The World Wide Web gained even more steam with the release of the Mosaic browser in 1993, which allowed graphics and text to be combined together as a way to present information and navigate the Internet. The Mosaic browser took off in popularity and was soon superseded by Netscape Navigator, the first commercial web browser, in 1994. The Internet and the World Wide Web were now poised for growth. The chart below shows the growth in users from the early days until now.
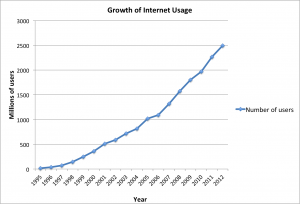
Growth of internet usage, 1995–2012 . Data taken from InternetWorldStats.com.
The Dot-Com Bubble
In the 1980s and early 1990s, the Internet was being managed by the National Science Foundation (NSF). The NSF had restricted commercial ventures on the Internet, which meant that no one could buy or sell anything online. In 1991, the NSF transferred its role to three other organizations, thus getting the US government out of direct control over the Internet and essentially opening up commerce online.
This new commercialization of the Internet led to what is now known as the dot-com bubble. A frenzy of investment in new dot-com companies took place in the late 1990s, running up the stock market to new highs on a daily basis. This investment bubble was driven by the fact that investors knew that online commerce would change everything. Unfortunately, many of these new companies had poor business models and ended up with little to show for all of the funds that were invested in them. In 2000 and 2001, the bubble burst and many of these new companies went out of business. Many companies also survived, including the still-thriving Amazon (started in 1994) and eBay (1995). After the dot-com bubble burst, a new reality became clear: in order to succeed online, e-business companies would need to develop real business models and show that they could survive financially using this new technology.
Web 2.0
In the first few years of the World Wide Web, creating and putting up a website required a specific set of knowledge: you had to know how to set up a server on the World Wide Web, how to get a domain name, how to write web pages in HTML, and how to troubleshoot various technical issues as they came up. Someone who did these jobs for a website became known as a webmaster.
As the web gained in popularity, it became more and more apparent that those who did not have the skills to be a webmaster still wanted to create online content and have their own piece of the web. This need was met with new technologies that provided a website framework for those who wanted to put content online. Blogger and Wikipedia are examples of these early Web 2.0 applications, which allowed anyone with something to say a place to go and say it, without the need for understanding HTML or web-server technology.
Starting in the early 2000s, Web 2.0 applications began a second bubble of optimism and investment. It seemed that everyone wanted their own blog or photo-sharing site. Here are some of the companies that came of age during this time: MySpace (2003), Photobucket (2003), Flickr (2004), Facebook (2004), WordPress (2005), Tumblr (2006), and Twitter (2006). The ultimate indication that Web 2.0 had taken hold was when Time magazine named “You” its “Person of the Year” in 2006.
Sidebar: E-mail Is the “Killer” App for the Internet
When the personal computer was created, it was a great little toy for technology hobbyists and armchair programmers. As soon as the spreadsheet was invented, however, businesses took notice, and the rest is history. The spreadsheet was the killer app for the personal computer: people bought PCs just so they could run spreadsheets.
The Internet was originally designed as a way for scientists and researchers to share information and computing power among themselves. However, as soon as electronic mail was invented, it began driving demand for the Internet. This wasn’t what the developers had in mind, but it turned out that people connecting to people was the killer app for the Internet.
We are seeing this again today with social networks, specifically Facebook. Many who weren’t convinced to have an online presence now feel left out without a Facebook account. The connections made between people using Web 2.0 applications like Facebook on their personal computer or smartphone is driving growth yet again.
Sidebar: The Internet and the World Wide Web Are Not the Same Thing
Many times, the terms “Internet” and “World Wide Web,” or even just “the web,” are used interchangeably. But really, they are not the same thing at all! The Internet is an interconnected network of networks. Many services run across the Internet: electronic mail, voice and video, file transfers, and, yes, the World Wide Web.
The World Wide Web is simply one piece of the Internet. It is made up of web servers that have HTML pages that are being viewed on devices with web browsers. It is really that simple.
The Growth of Broadband
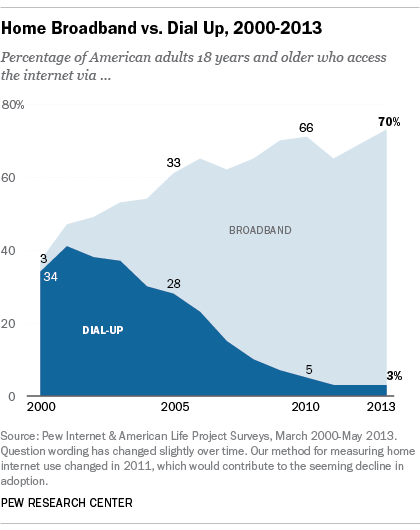
In the early days of the Internet, most access was done via a modem over an analog telephone line. A modem (short for “modulator-demodulator”) was connected to the incoming phone line and a computer in order to connect you to a network. Speeds were measured in bits-per-second (bps), with speeds growing from 1200 bps to 56,000 bps over the years. Connection to the Internet via these modems is called dial-up access. Dial-up was very inconvenient because it tied up the phone line. As the web became more and more interactive, dial-up also hindered usage, as users wanted to transfer more and more data. As a point of reference, downloading a typical 3.5 mb song would take 24 minutes at 1200 bps and 2 minutes at 28,800 bps.
A broadband connection is defined as one that has speeds of at least 256,000 bps, though most connections today are much faster, measured in millions of bits per second (megabits or mbps) or even billions (gigabits). For the home user, a broadband connection is usually accomplished via the cable television lines or phone lines (DSL). Both cable and DSL have similar prices and speeds, though each individual may find that one is better than the other for their specific area. Speeds for cable and DSL can vary during different times of the day or week, depending upon how much data traffic is being used. In more remote areas, where cable and phone companies do not provide access, home Internet connections can be made via satellite. The average home broadband speed is anywhere between 3 mbps and 30 mbps. At 10 mbps, downloading a typical 3.5 mb song would take less than a second. For businesses who require more bandwidth and reliability, telecommunications companies can provide other options, such as T1 and T3 lines.
Broadband access is important because it impacts how the Internet is used. When a community has access to broadband, it allows them to interact more online and increases the usage of digital tools overall. Access to broadband is now considered a basic human right by the United Nations, as declared in their 2011 statement:
“Broadband technologies are fundamentally transforming the way we live,” the Broadband Commission for Digital Development, set up last year by the UN Educational Scientific and Cultural Organization (UNESCO) and the UN International Telecommunications Union (ITU), said in issuing “The Broadband Challenge” at a leadership summit in Geneva.
“It is vital that no one be excluded from the new global knowledge societies we are building. We believe that communication is not just a human need – it is a right.”[1]
Wireless Networking
Today we are used to being able to access the Internet wherever we go. Our smartphones can access the Internet; Starbucks provides wireless “hotspots” for our laptops or iPads. These wireless technologies have made Internet access more convenient and have made devices such as tablets and laptops much more functional. Let’s examine a few of these wireless technologies.
Wi-Fi
Wi-Fi is a technology that takes an Internet signal and converts it into radio waves. These radio waves can be picked up within a radius of approximately 65 feet by devices with a wireless adapter. Several Wi-Fi specifications have been developed over the years, starting with 802.11b (1999), followed by the 802.11g specification in 2003 and 802.11n in 2009. Each new specification improved the speed and range of Wi-Fi, allowing for more uses. One of the primary places where Wi-Fi is being used is in the home. Home users are purchasing Wi-Fi routers, connecting them to their broadband connections, and then connecting multiple devices via Wi-Fi.
Mobile Network
As the cellphone has evolved into the smartphone, the desire for Internet access on these devices has led to data networks being included as part of the mobile phone network. While Internet connections were technically available earlier, it was really with the release of the 3G networks in 2001 (2002 in the US) that smartphones and other cellular devices could access data from the Internet. This new capability drove the market for new and more powerful smartphones, such as the iPhone, introduced in 2007. In 2011, wireless carriers began offering 4G data speeds, giving the cellular networks the same speeds that customers were used to getting via their home connection.
Sidebar: Why Doesn’t My Cellphone Work When I Travel Abroad?
As mobile phone technologies have evolved, providers in different countries have chosen different communication standards for their mobile phone networks. In the US, both of the two competing standards exist: GSM (used by AT&T and T-Mobile) and CDMA (used by the other major carriers). Each standard has its pros and cons, but the bottom line is that phones using one standard cannot easily switch to the other. In the US, this is not a big deal because mobile networks exist to support both standards. But when you travel to other countries, you will find that most of them use GSM networks, with the one big exception being Japan, which has standardized on CDMA. It is possible for a mobile phone using one type of network to switch to the other type of network by switching out the SIM card, which controls your access to the mobile network. However, this will not work in all cases. If you are traveling abroad, it is always best to consult with your mobile provider to determine the best way to access a mobile network.
Bluetooth

While Bluetooth is not generally used to connect a device to the Internet, it is an important wireless technology that has enabled many functionalities that are used every day. When created in 1994 by Ericsson, it was intended to replace wired connections between devices. Today, it is the standard method for connecting nearby devices wirelessly. Bluetooth has a range of approximately 300 feet and consumes very little power, making it an excellent choice for a variety of purposes. Some applications of Bluetooth include: connecting a printer to a personal computer, connecting a mobile phone and headset, connecting a wireless keyboard and mouse to a computer, and connecting a remote for a presentation made on a personal computer.
VoIP
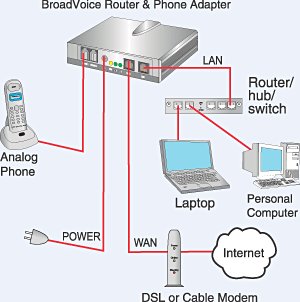
A typical VoIP communication. Image courtesy of BroadVoice.
A growing class of data being transferred over the Internet is voice data. A protocol called voice over IP, or VoIP, enables sounds to be converted to a digital format for transmission over the Internet and then re-created at the other end. By using many existing technologies and software, voice communication over the Internet is now available to anyone with a browser (think Skype, Google Hangouts). Beyond this, many companies are now offering VoIP-based telephone service for business and home use.
Organizational Networking
LAN and WAN
While the Internet was evolving and creating a way for organizations to connect to each other and the world, another revolution was taking place inside organizations. The proliferation of personal computers inside organizations led to the need to share resources such as printers, scanners, and data. Organizations solved this problem through the creation of local area networks (LANs), which allowed computers to connect to each other and to peripherals. These same networks also allowed personal computers to hook up to legacy mainframe computers.
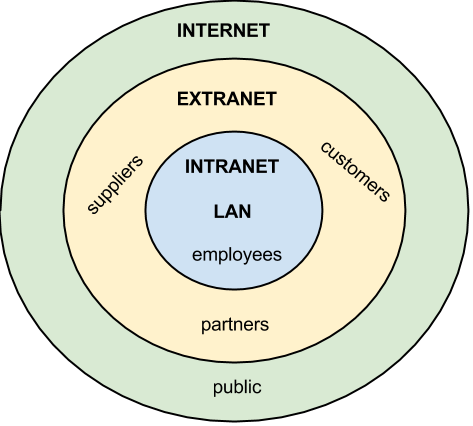
Scope of business networks
An LAN is (by definition) a local network, usually operating in the same building or on the same campus. When an organization needed to provide a network over a wider area (with locations in different cities or states, for example), they would build a wide area network (WAN).
Client-Server
The personal computer originally was used as a stand-alone computing device. A program was installed on the computer and then used to do word processing or number crunching. However, with the advent of networking and local area networks, computers could work together to solve problems. Higher-end computers were installed as servers, and users on the local network could run applications and share information among departments and organizations. This is called client-server computing.
Intranet
Just as organizations set up web sites to provide global access to information about their business, they also set up internal web pages to provide information about the organization to the employees. This internal set of web pages is called an intranet. Web pages on the intranet are not accessible to those outside the company; in fact, those pages would come up as “not found” if an employee tried to access them from outside the company’s network.
Extranet
Sometimes an organization wants to be able to collaborate with its customers or suppliers while at the same time maintaining the security of being inside its own network. In cases like this a company may want to create an extranet, which is a part of the company’s network that can be made available securely to those outside of the company. Extranets can be used to allow customers to log in and check the status of their orders, or for suppliers to check their customers’ inventory levels.
Sometimes, an organization will need to allow someone who is not located physically within its internal network to gain access. This access can be provided by a virtual private network (VPN). VPNs will be discussed further in the chapter 6 (on information security).
Sidebar: Microsoft’s SharePoint Powers the Intranet
As organizations begin to see the power of collaboration between their employees, they often look for solutions that will allow them to leverage their intranet to enable more collaboration. Since most companies use Microsoft products for much of their computing, it is only natural that they have looked to Microsoft to provide a solution. This solution is Microsoft’s SharePoint.
SharePoint provides a communication and collaboration platform that integrates seamlessly with Microsoft’s Office suite of applications. Using SharePoint, employees can share a document and edit it together – no more e-mailing that Word document to everyone for review. Projects and documents can be managed collaboratively across the organization. Corporate documents are indexed and made available for search. No more asking around for that procedures document – now you just search for it in SharePoint. For organizations looking to add a social networking component to their intranet, Microsoft offers Yammer, which can be used by itself or integrated into SharePoint.
Cloud Computing
We covered cloud computing in chapter 3, but it should also be mentioned here. The universal availability of the Internet combined with increases in processing power and data-storage capacity have made cloud computing a viable option for many companies. Using cloud computing, companies or individuals can contract to store data on storage devices somewhere on the Internet. Applications can be “rented” as needed, giving a company the ability to quickly deploy new applications. You can read about cloud computing in more detail in chapter 3.
Sidebar: Metcalfe’s Law
Just as Moore’s Law describes how computing power is increasing over time, Metcalfe’s Law describes the power of networking. Specifically, Metcalfe’s Law states that the value of a telecommunications network is proportional to the square of the number of connected users of the system. Think about it this way: If none of your friends were on Facebook, would you spend much time there? If no one else at your school or place of work had e-mail, would it be very useful to you? Metcalfe’s Law tries to quantify this value.
Summary
The networking revolution has completely changed how the computer is used. Today, no one would imagine using a computer that was not connected to one or more networks. The development of the Internet and World Wide Web, combined with wireless access, has made information available at our fingertips. The Web 2.0 revolution has made us all authors of web content. As networking technology has matured, the use of Internet technologies has become a standard for every type of organization. The use of intranets and extranets has allowed organizations to deploy functionality to employees and business partners alike, increasing efficiencies and improving communications. Cloud computing has truly made information available everywhere and has serious implications for the role of the IT department.
Study Questions
- What were the first four locations hooked up to the Internet (ARPANET)?
- What does the term packet mean?
- Which came first, the Internet or the World Wide Web?
- What was revolutionary about Web 2.0?
- What was the so-called killer app for the Internet?
- What makes a connection a broadband connection?
- What does the term VoIP mean?
- What is an LAN?
- What is the difference between an intranet and an extranet?
- What is Metcalfe’s Law?
Exercises
- What is the IP address of your computer? How did you find out? What is the IP address of google.com? How did you find out? Did you get IPv4 or IPv6 addresses?
- What is the difference between the Internet and the World Wide Web? Create at least three statements that identify the differences between the two.
- Who are the broadband providers in your area? What are the prices and speeds offered?
- Pretend you are planning a trip to three foreign countries in the next month. Consult your wireless carrier to determine if your mobile phone would work properly in those countries. What would the costs be? What alternatives do you have if it would not work?
- "UN sets goal of bringing broadband to half developing world’s people by 2015.", UN News Center website, http://www.un.org/apps/news/story.as...1#.Ut7JOmTTk1J↵