6: Information Systems Security
- Page ID
- 4313
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Learning Objectives
Upon successful completion of this chapter, you will be able to:
- identify the information security triad;
- identify and understand the high-level concepts surrounding information security tools; and
- secure yourself digitally.
Introduction
As computers and other digital devices have become essential to business and commerce, they have also increasingly become a target for attacks. In order for a company or an individual to use a computing device with confidence, they must first be assured that the device is not compromised in any way and that all communications will be secure. This chapter reviews the fundamental concepts of information systems security and discusses some of the measures that can be taken to mitigate security threats. The chapter begins with an overview focusing on how organizations can stay secure. Several different measures that a company can take to improve security will be discussed. Finally, you will review a list of security precautions that individuals can take in order to secure their personal computing environment.
The Information Security Triad: Confidentiality, Integrity, Availability (CIA)
Confidentiality
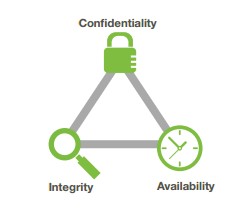
Protecting information means you want to want to be able to restrict access to those who are allowed to see it. This is sometimes referred to as NTK, Need to Know. Everyone else should be disallowed from learning anything about its contents. This is the essence of confidentiality. For example, federal law requires that universities restrict access to private student information. Access to grade records should be limited to those who have authorized access.
Integrity
Integrity is the assurance that the information being accessed has not been altered and truly represents what is intended. Just as a person with integrity means what he or she says and can be trusted to consistently represent the truth, information integrity means information truly represents its intended meaning. Information can lose its integrity through malicious intent, such as when someone who is not authorized makes a change to intentionally misrepresent something. An example of this would be when a hacker is hired to go into the university’s system and change a student’s grade.
Integrity can also be lost unintentionally, such as when a computer power surge corrupts a file or someone authorized to make a change accidentally deletes a file or enters incorrect information.
Availability
Information availability is the third part of the CIA triad. Availability means information can be accessed and modified by anyone authorized to do so in an appropriate timeframe. Depending on the type of information, appropriate timeframe can mean different things. For example, a stock trader needs information to be available immediately, while a sales person may be happy to get sales numbers for the day in a report the next morning. Online retailers require their servers to be available twenty-four hours a day, seven days a week. Other companies may not suffer if their web servers are down for a few minutes once in a while.
Tools for Information Security
In order to ensure the confidentiality, integrity, and availability of information, organizations can choose from a variety of tools. Each of these tools can be utilized as part of an overall information-security policy.
Authentication
The most common way to identify someone is through their physical appearance, but how do we identify someone sitting behind a computer screen or at the ATM? Tools for authentication are used to ensure that the person accessing the information is, indeed, who they present themselves to be.
Authentication can be accomplished by identifying someone through one or more of three factors:
- Something they know,
- Something they have, or
- Something they are.
For example, the most common form of authentication today is the user ID and password. In this case, the authentication is done by confirming something that the user knows (their ID and password). But this form of authentication is easy to compromise (see sidebar) and stronger forms of authentication are sometimes needed. Identifying someone only by something they have, such as a key or a card, can also be problematic. When that identifying token is lost or stolen, the identity can be easily stolen. The final factor, something you are, is much harder to compromise. This factor identifies a user through the use of a physical characteristic, such as a retinal scan, fingerprint, or facial geometry. Identifying someone through their physical characteristics is called biometrics.

A more secure way to authenticate a user is through multi-factor authentication. By combining two or more of the factors listed above, it becomes much more difficult for someone to misrepresent themselves. An example of this would be the use of an RSA SecurID token. The RSA device is something you have, and it generates a new access code every sixty seconds. To log in to an information resource using the RSA device, you combine something you know, such as a four-digit PIN, with the code generated by the device. The only way to properly authenticate is by both knowing the code and having the RSA device.
Access Control
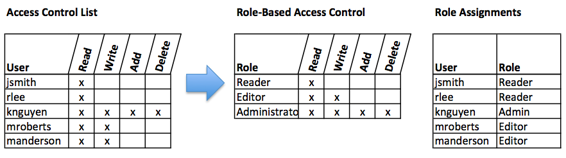
Once a user has been authenticated, the next step is to ensure that they can only access the information resources that are appropriate. This is done through the use of access control. Access control determines which users are authorized to read, modify, add, and/or delete information. Several different access control models exist. Two of the more common are: the Access Control List (ACL) and Role-Based Access Control (RBAC).
An information security employee can produce an ACL which identifies a list of users who have the capability to take specific actions with an information resource such as data files. Specific permissions are assigned to each user such as read, write, delete, or add. Only users with those permissions are allowed to perform those functions.
ACLs are simple to understand and maintain, but there are several drawbacks. The primary drawback is that each information resource is managed separately, so if a security administrator wanted to add or remove a user to a large set of information resources, it would be quite difficult. And as the number of users and resources increase, ACLs become harder to maintain. This has led to an improved method of access control, called role-based access control, or RBAC. With RBAC, instead of giving specific users access rights to an information resource, users are assigned to roles and then those roles are assigned the access. This allows the administrators to manage users and roles separately, simplifying administration and, by extension, improving security.
The following image shows an ACL with permissions granted to individual users. RBAC allows permissions to be assigned to roles, as shown in the middle grid, and then in the third grid each user is assigned a role. Although not modeled in the image, each user can have multiple roles such as Reader and Editor.
Sidebar: Password Security
So why is using just a simple user ID and password not considered a secure method of authentication? It turns out that this single-factor authentication is extremely easy to compromise. Good password policies must be put in place in order to ensure that passwords cannot be compromised. Below are some of the more common policies that organizations should use.
- Require complex passwords. One reason passwords are compromised is that they can be easily guessed. A recent study found that the top three passwords people used were password, 123456 and 12345678.[1] A password should not be simple, or a word that can be found in a dictionary. Hackers first attempt to crack a password by testing every term in the dictionary. Instead, a good password policy should require the use of a minimum of eight characters, at least one upper-case letter, one special character, and one digit.
- Change passwords regularly. It is essential that users change their passwords on a regular basis. Also, passwords may not be reused. Users should change their passwords every sixty to ninety days, ensuring that any passwords that might have been stolen or guessed will not be able to be used against the company.
- Train employees not to give away passwords. One of the primary methods used to steal passwords is to simply figure them out by asking the users for their password. Pretexting occurs when an attacker calls a helpdesk or security administrator and pretends to be a particular authorized user having trouble logging in. Then, by providing some personal information about the authorized user, the attacker convinces the security person to reset the password and tell him what it is. Another way that employees may be tricked into giving away passwords is through e-mail phishing. Phishing occurs when a user receives an e-mail that looks as if it is from a trusted source, such as their bank or employer. In the e-mail the user is asked to click a link and log in to a website that mimics the genuine website, then enter their ID and password. The userID and password are then captured by the attacker.
Encryption
Many times an organization needs to transmit information over the Internet or transfer it on external media such as a flash drive. In these cases, even with proper authentication and access control, it is possible for an unauthorized person to gain access to the data. Encryption is a process of encoding data upon its transmission or storage so that only authorized individuals can read it. This encoding is accomplished by software which encodes the plain text that needs to be transmitted (encryption). Then the recipient receives the cipher text and decodes it (decryption). In order for this to work, the sender and receiver need to agree on the method of encoding so that both parties have the same message. Known as symmetric key encryption, both parties share the encryption key, enabling them to encode and decode each other’s messages.
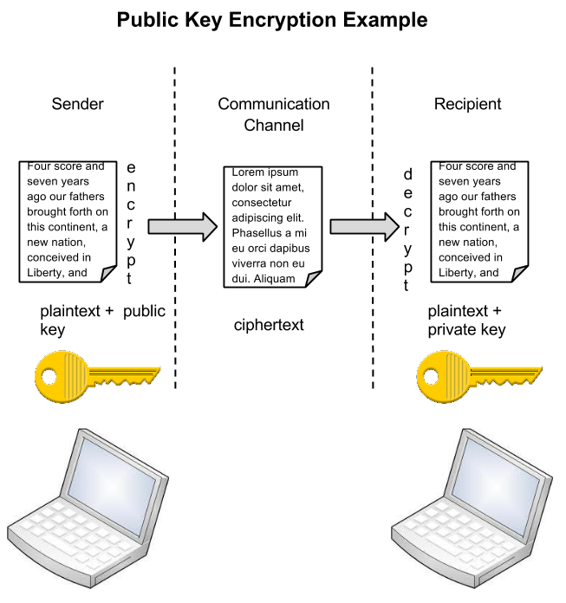
An alternative to symmetric key encryption is public key encryption. In public key encryption, two keys are used: a public key and a private key. To send an encrypted message, you obtain the public key, encode the message, and send it. The recipient then uses their private key to decode it. The public key can be given to anyone who wishes to send the recipient a message. Each user simply needs one private key and one public key in order to secure messages. The private key is necessary in order to decrypt a message sent with the public key.
Notice in the image how the sender on the left creates a plaintext message which is then encrypted with a public key. The ciphered text is transmitted through the communication channel and the recipient uses their private key to decrypt the message and then read the plain text.
Sidebar: Blockchain and Bitcoin
Blockchain
Introduced in 2008 as part of a proposal for Bitcoin, Blockchain is a peer-to-peer network which provides an open, distributed record of transactions between two parties. A “peer-to-peer” network is one where there is no server between the two nodes trying to communicate. Essentially, this means that each node acts as a server and a client.
Supporters see blockchain as a tool to simplify all types of transactions: payments, contracts, etc. Motivation comes from the desire to remove the middleman (lawyer, banker, broker) from transactions, making them more efficient and readily available across the Internet. Blockchain is already being used to track products through supply chains.
Blockchain is considered a foundational technology, potentially creating new foundations in economics and social systems. There are numerous concerns about Blockchain and its adoption. Consider the following:
- Speed of adoption. Initially there is a great deal of enthusiasm by a small group. However, adoption on a larger scale can take a great number of years even decades for a worldwide acceptance of a new method of doing business.
- Governance. The banking sector, both in individual countries (U. S. Federal Reserve System) and the world at large (the International Monetary Fund), controls financial transactions. One purpose of these organizations is an attempt to avoid banking and financial systems collapse. Blockchain will result in the governance of financial transactions shifting away from these government-controlled institutions.
- Smart contracts. The smart contract will re-shape how businesses interact. It is possible for blockchain to automatically send payment to a vendor the instant the product is delivered to the customer. Such “self-executing” contracts are already taking place in banking and venture capital funding. [9]
Many are forecasting some universal form of payment or value transfer for business transactions. Blockchain and Bitcoin are being used to transform banking in various locations around the world. The following Bitcoin section includes a look at a new banking venture in Tanzania, East Africa.
Bitcoin


Bitcoin logo
Bitcoin is a world wide payment system using cryptocurrency. It functions without a central bank, operating as a peer-to-peer network with transactions happening directly between vendors and buyers. Records for transactions are recorded in the blockchain. Bitcoin technology was released in 2009. The University of Cambridge estimated there were 2.9 and 5.8 million unique users of bitcoin in 2017.[10] This web site provides more information about bitcoin.
A major bitcoin project is underway in Tanzania. Business transactions in this East African country are fraught with many challenges such as counterfeit currency and a 28% transaction fee on individuals who do not have a bank account. Seventy percent of the country’s population fall into this category. Benjamin Fernandes, a Tanzanian and 2017 graduate of Stanford Graduate School of Business, is co-founder of NALA, a Tanzanian firm working to bring cryptocurrency to a country where 96% of the population have access to mobile devices. NALA’s goal is to provide low cost transactions to all of the country’s citizens through cryptocurrency.[11] You can read more of this cryptocurrency venture here.
Backups
Another essential tool for information security is a comprehensive backup plan for the entire organization. Not only should the data on the corporate servers be backed up, but individual computers used throughout the organization should also be backed up. A good backup plan should consist of several components.
- Full understanding of the organization’s information resources. What information does the organization actually have? Where is it stored? Some data may be stored on the organization’s servers, other data on users’ hard drives, some in the cloud, and some on third-party sites. An organization should make a full inventory of all of the information that needs to be backed up and determine the best way to back it up.
- Regular backups of all data. The frequency of backups should be based on how important the data is to the company, combined with the ability of the company to replace any data that is lost. Critical data should be backed up daily, while less critical data could be backed up weekly. Most large organizations today use data redundancy so their records are always backed up.
- Offsite storage of backup data sets. If all backup data is being stored in the same facility as the original copies of the data, then a single event such as an earthquake, fire, or tornado would destroy both the original data and the backup. It is essential the backup plan includes storing the data in an offsite location.
- Test of data restoration. Backups should be tested on a regular basis by having test data deleted then restored from backup. This will ensure that the process is working and will give the organization confidence in the backup plan.
Besides these considerations, organizations should also examine their operations to determine what effect downtime would have on their business. If their information technology were to be unavailable for any sustained period of time, how would it impact the business?
Additional concepts related to backup include the following:
- Uninterruptible Power Supply (UPS). A UPS provides battery backup to critical components of the system, allowing them to stay online longer and/or allowing the IT staff to shut them down using proper procedures in order to prevent data loss that might occur from a power failure.
- Alternate, or “hot” sites. Some organizations choose to have an alternate site where an exact replica of their critical data is always kept up to date. When the primary site goes down, the alternate site is immediately brought online so that little or no downtime is experienced.
As information has become a strategic asset, a whole industry has sprung up around the technologies necessary for implementing a proper backup strategy. A company can contract with a service provider to back up all of their data or they can purchase large amounts of online storage space and do it themselves. Technologies such as Storage Area Networks (SAN) and archival systems are now used by most large businesses for data backup.
Firewalls
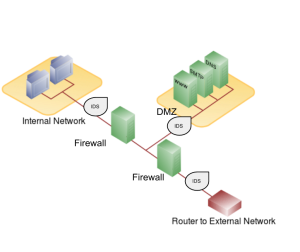
Firewalls are another method that an organization can use for increasing security on its network. A firewall can exist as hardware or software, or both. A hardware firewall is a device that is connected to the network and filters the packets based on a set of rules. One example of these rules would be preventing packets entering the local network that come from unauthorized users. A software firewall runs on the operating system and intercepts packets as they arrive to a computer.
A firewall protects all company servers and computers by stopping packets from outside the organization’s network that do not meet a strict set of criteria. A firewall may also be configured to restrict the flow of packets leaving the organization. This may be done to eliminate the possibility of employees watching YouTube videos or using Facebook from a company computer.
A demilitarized zone (DMZ) implements multiple firewalls as part of network security configuration, creating one or more sections of their network that are partially secured. The DMZ typically contains resources that need broader access but still need to be secured.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) can be placed on the network for security purposes. An IDS does not add any additional security. Instead, it provides the capability to identify if the network is being attacked. An IDS can be configured to watch for specific types of activities and then alert security personnel if that activity occurs. An IDS also can log various types of traffic on the network for analysis later. It is an essential part of any good security system.
Sidebar: Virtual Private Networks
Using firewalls and other security technologies, organizations can effectively protect many of their information resources by making them invisible to the outside world. But what if an employee working from home requires access to some of these resources? What if a consultant is hired who needs to do work on the internal corporate network from a remote location? In these cases, a Virtual Private Network (VPN) is needed.
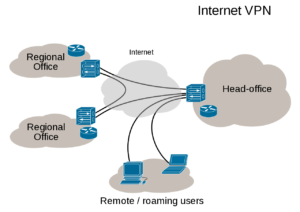
A VPN allows a user who is outside of a corporate network to take a detour around the firewall and access the internal network from the outside. Through a combination of software and security measures, a VPN provides off-site access to the organization’s network while ensuring overall security.
The Internet cloud is essentially an insecure channel through which people communicate to various web sites/servers. Implementing a VPN results in a secure pathway, usually referred to as a tunnel, through the insecure cloud, virtually guaranteeing secure access to the organization’s resources. The diagram represents security by way of the functionality of a VPN as it “tunnels” through the insecure Internet Cloud. Notice that the remote user is given access to the organization’s intranet, as if the user was physically located within the intranet.
Physical Security
An organization can implement the best authentication scheme in the world, develop superior access control, and install firewalls and intrusion detection, but its security cannot be complete without implementation of physical security. Physical security is the protection of the actual hardware and networking components that store and transmit information resources. To implement physical security, an organization must identify all of the vulnerable resources and take measures to ensure that these resources cannot be physically tampered with or stolen. These measures include the following.
- Locked doors. It may seem obvious, but all the security in the world is useless if an intruder can simply walk in and physically remove a computing device. High value information assets should be secured in a location with limited access.
- Physical intrusion detection. High value information assets should be monitored through the use of security cameras and other means to detect unauthorized access to the physical locations where they exist.
- Secured equipment. Devices should be locked down to prevent them from being stolen. One employee’s hard drive could contain all of your customer information, so it is essential that it be secured.
- Environmental monitoring. An organization’s servers and other high value equipment should always be kept in a room that is monitored for temperature, humidity, and airflow. The risk of a server failure rises when these factors exceed acceptable ranges.
- Employee training. One of the most common ways thieves steal corporate information is the theft of employee laptops while employees are traveling. Employees should be trained to secure their equipment whenever they are away from the office.
Security Policies
Besides the technical controls listed above, organizations also need to implement security policies as a form of administrative control. In fact, these policies should really be a starting point in developing an overall security plan. A good information security policy lays out the guidelines for employee use of the information resources of the company and provides the company recourse in the event that an employee violates a policy.
According to the SANS Institute, a good policy is “a formal, brief, and high-level statement or plan that embraces an organization’s general beliefs, goals, objectives, and acceptable procedures for a specified subject area.” Policies require compliance. Failure to comply with a policy will result in disciplinary action. A policy does not list the specific technical details, instead it focuses on the desired results. A security policy should be based on the guiding principles of confidentiality, integrity, and availability.[2]
Web use is a familiar example of a security policy. A web use policy lays out the responsibilities of company employees as they use company resources to access the Internet. A good example of a web use policy is included in Harvard University’s “Computer Rules and Responsibilities” policy, which can be found here.
A security policy should also address any governmental or industry regulations that apply to the organization. For example, if the organization is a university, it must be aware of the Family Educational Rights and Privacy Act (FERPA), which restricts access to student information. Health care organizations are obligated to follow several regulations, such as the Health Insurance Portability and Accountability Act (HIPAA).
A good resource for learning more about security policies is the SANS Institute’s Information Security Policy Page.
Sidebar: Mobile Security
As the use of mobile devices such as laptops and smartphones proliferates, organizations must be ready to address the unique security concerns that the use of these devices bring. One of the first questions an organization must consider is whether to allow mobile devices in the workplace at all. Many employees already have these devices, so the question becomes: Should we allow employees to bring their own devices and use them as part of their employment activities? Or should we provide the devices to our employees? Creating a BYOD (“Bring Your Own Device”) policy allows employees to integrate themselves more fully into their job and can bring higher employee satisfaction and productivity. In many cases, it may be virtually impossible to prevent employees from having their own smartphones or laptops in the workplace. If the organization provides the devices to its employees, it gains more control over use of the devices, but it also increases the burden of having to administrate distribution and use.
Mobile devices can pose many unique security challenges to an organization. Probably one of the biggest concerns is theft of intellectual property. For an employee with malicious intent, it would be a very simple process to connect a mobile device either to a computer via the USB port, or wirelessly to the corporate network, and download confidential data. It would also be easy to secretly take a high-quality picture using a built-in camera.
When an employee does have permission to access and save company data on his or her device, a different security threat emerges. Namely, that device now becomes a target for thieves. Theft of mobile devices (in this case, including laptops) is one of the primary methods that data thieves use.
So what can be done to secure mobile devices? Begin with a good policy regarding their use. According to a 2013 SANS study, organizations should consider developing a mobile device policy that addresses the following issues: use of the camera, use of voice recording, application purchases, encryption at rest, Wi-Fi autoconnect settings, Bluetooth settings, VPN use, password settings, lost or stolen device reporting, and backup. [3]
Besides policies, there are several different tools that an organization can use to mitigate some of these risks. For example, if a device is stolen or lost, geolocation software can help the organization find it. In some cases, it may even make sense to install remote data removal software, which will remove data from a device if it becomes a security risk.
Usability
When looking to secure information resources, organizations must balance the need for security with users’ needs to effectively access and use these resources. If a system’s security measures make it difficult to use, then users will find ways around the security, which may make the system more vulnerable than it would have been without the security measures. Consider password policies. If the organization requires an extremely long password with several special characters, an employee may resort to writing it down and putting it in a drawer since it will be impossible to memorize.
Personal Information Security

As a final topic for this chapter, consider what measures each of us, as individual users, can take to secure our computing technologies. There is no way to have 100% security, but there are several simple steps each individual can take to be more secure.
- Keep your software up to date. Whenever a software vendor determines that a security flaw has been found in their software, an update will be released so you can download the patch to fix the problem. You should turn on automatic updating on your computer to automate this process.
- Install antivirus software and keep it up to date. There are many good antivirus software packages on the market today, including some that are free.
- Be smart about your connections. You should be aware of your surroundings. When connecting to a Wi-Fi network in a public place, be aware that you could be at risk of being spied on by others sharing that network. It is advisable not to access your financial or personal data while attached to a Wi-Fi hotspot. You should also be aware that connecting USB flash drives to your device could also put you at risk. Do not attach an unfamiliar flash drive to your device unless you can scan it first with your security software.
- Backup your data. Just as organizations need to backup their data, individuals need to so as well. The same rules apply. Namely, do it regularly and keep a copy of it in another location. One simple solution for this is to set up an account with an online backup service to automate your backups.
- Secure your accounts with two-factor authentication. Most e-mail and social media providers now have a two-factor authentication option. When you log in to your account from an unfamiliar computer for the first time, it sends you a text message with a code that you must enter to confirm that you are really you. This means that no one else can log in to your accounts without knowing your password and having your mobile phone with them.
- Make your passwords long, strong, and unique. Your personal passwords should follow the same rules that are recommended for organizations. Your passwords should be long (at least 12 random characters) and contain at least two of the following: uppercase and lowercase letters, digits, and special characters. Passwords should not include words that could be tied to your personal information, such as the name of your pet. You also should use different passwords for different accounts, so that if someone steals your password for one account, they still are locked out of your other accounts.
- Be suspicious of strange links and attachments. When you receive an e-mail, tweet, or Facebook post, be suspicious of any links or attachments included there. Do not click on the link directly if you are at all suspicious. Instead, if you want to access the website, find it yourself with your browser and navigate to it directly. The I Love You virus was distributed via email in May 2000 and contained an attachment which when opened copied itself into numerous folders on the user’s computer and modified the operating system settings. An estimated 50,000 computers were affected, all of which could have been avoided if users had followed the warning to not open the attachment.
You can find more about these steps and many other ways to be secure with your computing by going to Stop. Think. Connect. This website is part of a campaign by the STOP. THINK. CONNECT. Messaging Convention in partnership with the U.S. government, including the White House.
Summary
As computing and networking resources have become more an integral part of business, they have also become a target of criminals. Organizations must be vigilant with the way they protect their resources. The same holds true for individuals. As digital devices become more intertwined in everyone’s life, it becomes crucial for each person to understand how to protect themselves.
Study Questions
- Briefly define each of the three members of the information security triad.
- What does the term authentication mean?
- What is multi-factor authentication?
- What is role-based access control?
- What is the purpose of encryption?
- What are two good examples of a complex password?
- What is pretexting?
- What are the components of a good backup plan?
- What is a firewall?
- What does the term physical security mean?
Exercises
- Describe one method of multi-factor authentication that you have experienced and discuss the pros and cons of using multi-factor authentication.
- What are some of the latest advances in encryption technologies? Conduct some independent research on encryption using scholarly or practitioner resources, then write a two- to three-page paper that describes at least two new advances in encryption technology.
- Find favorable and unfavorable articles about both blockchain and bitcoin. Report your findings, then state your own opinion about these technologies
- What is the password policy at your place of employment or study? Do you have to change passwords every so often? What are the minimum requirements for a password?
- When was the last time you backed up your data? What method did you use? In one to two pages, describe a method for backing up your data. Ask your instructor if you can get extra credit for backing up your data.
- Find the information security policy at your place of employment or study. Is it a good policy? Does it meet the standards outlined in the chapter?
- How diligent are you in keeping your own information secure? Review the steps listed in the chapter and comment on your security status.
Labs
- The Caesar Cipher. One of the oldest methods of encryption was used by Julius Caesar and involved simply shifting text a specified number of positions in the alphabet. The number of shifted positions is known as the key. So a key = 3 would encrypt ZOO to CRR. Decrypt the following message which has a key = 3: FRPSXWHU
- The Vigenere Cipher. This cipher was used as recently as the Civil War by the Confederate forces. The key is slightly more complex than the Caesar Cipher. Vigenere used the number of letters after ‘A’ for his key. For example, if the key = COD, the first letter in the cypher is shifted 2 characters (because “C” is 2 letters after the letter ‘A’), the second letter is shifted 14 letters (O being 14 letters after ‘A’), and the third letter is shifted 3 letters (D being 3 letters after ‘A’). Then the pattern is repeated for subsequent letters. Decrypt the following message which has a key = COD: YSPGSWCHGCKQ
- Frequency and Pattern Analysis. If you’ve ever watched Wheel of Fortune you know that contestants look for patterns and frequencies in trying to solve a puzzle. Your job in this lab is to analyze letter frequency and letter patterns to determine the plaintext message which in this case is a single word. The key is a simple substitution where the same letter in plaintext always results in the same letter in the cyphertext. The most frequently used letters in the English language are: E, A, O , I, T, S, N. Pattern analysis includes knowing words that have double letters such as “school.” Other patterns include “ing” at the end of a word, “qu” and “th” as a pairs of letters.Cyphertext = CAGGJWhat is the key and the plaintext?
- Gallagher, S. (2012, November 3). Born to be breached. Arstechnica. Retrieved from http://arstechnica.com/information-t...e-most-common/
- SANS Institute. (n.d.). Information Security Policy Templates. Retrieved from www.sans.org/security-resourc...icy_Primer.pdf on May 31, 2013.
- SANS. (n.d.). SCORE: Checklists and Step by Step Guides. Retrieved from www.sans.org/score/checklists...-checklist.xls
- Iansiti, M. and Lakhani, K. R. (2017, January). The truth about blockchain. Harvard Business Review. Retrieved from https://hbr.org/2017/01/the-truth-about-blockchain↵
- Wikipedia. (n.d.). Bitcoin. Harvard Business Review. Retrieved from https://en.Wikipedia.org/wiki/Bitcoin↵
- Fernandes, B. (2017, October 20). Personal telephone interview↵


